Top 10 Middleware Technologies: A Guide to Modern Software Architecture
Top 10 Middleware Technologies are the unsung heroes of modern software architecture, silently orchestrating the communication and data flow that power our digital world. From enabling seamless communication between services […]
Top 10 Middleware Technologies are the unsung heroes of modern software architecture, silently orchestrating the communication and data flow that power our digital world. From enabling seamless communication between services to enhancing security and performance, these technologies are the backbone of today’s complex applications.
This guide explores the top 10 middleware technologies, delving into their key features, benefits, and use cases. We’ll examine messaging queues, API gateways, service buses, data caching, load balancing, security middleware, and monitoring and logging technologies. By understanding these essential components, developers can build more robust, scalable, and secure applications.
Introduction to Middleware
Middleware is a software layer that sits between application programs and operating systems, facilitating communication and data exchange. It acts as an intermediary, enabling applications to interact with each other and access shared resources without direct knowledge of underlying systems.
Middleware plays a crucial role in modern software architectures by simplifying application development, enhancing performance, and improving scalability.
Benefits of Middleware
Middleware offers numerous benefits, including:
- Simplified Application Development: Middleware provides pre-built components and functionalities, reducing the need for developers to write complex code from scratch. This streamlines development processes and allows teams to focus on core business logic.
- Enhanced Performance: Middleware optimizes resource utilization and communication efficiency, leading to faster application response times and improved overall performance.
- Increased Scalability: Middleware facilitates horizontal scaling by enabling applications to distribute workloads across multiple servers, ensuring smooth performance even under heavy traffic.
- Improved Security: Middleware layers provide security features such as authentication, authorization, and data encryption, protecting applications and sensitive information from unauthorized access.
- Enhanced Interoperability: Middleware acts as a bridge between different platforms and technologies, allowing applications written in diverse languages and running on various operating systems to communicate seamlessly.
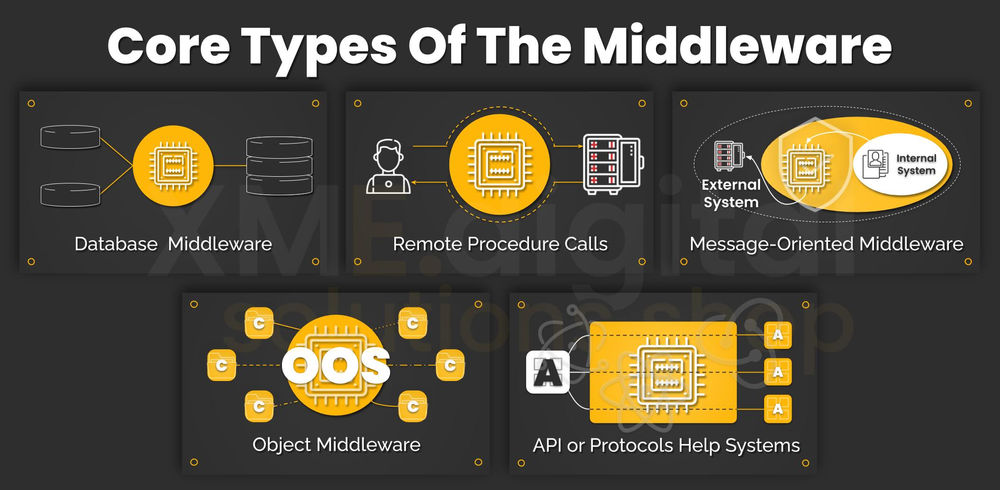
Common Middleware Categories
Middleware encompasses various categories, each addressing specific functionalities and needs:
- Message Queues: Message queues facilitate asynchronous communication between applications, decoupling senders and receivers. They store messages temporarily, ensuring reliable delivery even if the recipient is unavailable.
- API Gateways: API gateways act as a central point of control for accessing APIs, providing security, rate limiting, and traffic management functionalities. They simplify API consumption and enhance overall API security.
- Service Buses: Service buses enable communication between distributed services, facilitating message routing, transformation, and orchestration. They provide a robust and reliable framework for building microservices architectures.
Top 10 Middleware Technologies
Middleware technologies play a crucial role in modern software development, enabling seamless communication and data exchange between different applications and systems. These technologies act as intermediaries, simplifying complex interactions and enhancing overall application performance and scalability.
Top 10 Middleware Technologies
Middleware technologies are essential for connecting different applications and systems, facilitating seamless data exchange and communication. This list highlights the top 10 middleware technologies based on their popularity, market share, and overall impact on the software development landscape.
| Rank | Technology | Description | Key Features |
|---|---|---|---|
| 1 | Apache Kafka | Apache Kafka is a distributed streaming platform that enables real-time data processing and distribution. It acts as a message broker, facilitating communication between different applications and systems. |
|
| 2 | MuleSoft Anypoint Platform | MuleSoft Anypoint Platform is an integration platform as a service (iPaaS) that provides a comprehensive suite of tools for connecting applications and data sources. It offers a visual development environment, pre-built connectors, and a wide range of integration capabilities. |
|
| 3 | Red Hat JBoss EAP | Red Hat JBoss EAP is a Java EE application server that provides a runtime environment for deploying and managing Java applications. It offers a wide range of features, including enterprise JavaBeans (EJBs), servlets, and JavaServer Pages (JSPs). |
|
| 4 | IBM WebSphere | IBM WebSphere is a comprehensive middleware platform that provides a wide range of services, including application server, message queuing, and integration tools. It offers a robust and secure environment for deploying and managing enterprise applications. |
|
| 5 | Oracle WebLogic Server | Oracle WebLogic Server is a Java EE application server that provides a runtime environment for deploying and managing Java applications. It offers a wide range of features, including EJBs, servlets, and JSPs. |
|
| 6 | Microsoft Azure Service Bus | Microsoft Azure Service Bus is a cloud-based messaging service that enables reliable and scalable communication between applications. It offers features such as message queues, topics, and event hubs. |
|
| 7 | RabbitMQ | RabbitMQ is an open-source message broker that implements the Advanced Message Queuing Protocol (AMQP). It offers a robust and reliable messaging platform for various applications. |
|
| 8 | Apache ActiveMQ | Apache ActiveMQ is an open-source message broker that provides a robust and scalable messaging platform. It supports various messaging protocols, including JMS, AMQP, and STOMP. |
|
| 9 | TIBCO Software | TIBCO Software provides a comprehensive suite of middleware technologies, including messaging, integration, and analytics solutions. It offers a wide range of products and services for connecting applications and data sources. |
|
| 10 | Software AG | Software AG provides a comprehensive suite of middleware technologies, including integration, messaging, and API management solutions. It offers a wide range of products and services for connecting applications and data sources. |
|
Messaging Queues
Messaging queues are a fundamental component of modern distributed systems, enabling asynchronous communication between different parts of an application. They act as intermediaries, decoupling senders and receivers, allowing them to operate independently without blocking each other. This decoupling is crucial for building scalable, resilient, and flexible systems.
Popular Messaging Queue Technologies
Messaging queue technologies offer a variety of features and capabilities to cater to different use cases. Here are some of the most popular and widely used technologies:
- RabbitMQ: A robust and feature-rich messaging broker that supports various messaging patterns, including point-to-point, publish-subscribe, and request-reply. It’s known for its ease of use, reliability, and extensive plugin ecosystem.
- Kafka: Designed for high-throughput, low-latency messaging, Kafka is ideal for handling large volumes of data streams. It’s commonly used in real-time data processing, event streaming, and microservices architectures.
- ActiveMQ: A mature and versatile messaging broker that supports various protocols, including JMS (Java Message Service) and AMQP (Advanced Message Queuing Protocol). It offers a wide range of features, including message persistence, clustering, and security.
Comparison of Messaging Queue Technologies
The choice of messaging queue technology depends on the specific requirements of the application. Here’s a comparison of the three technologies discussed above:
| Feature | RabbitMQ | Kafka | ActiveMQ |
|---|---|---|---|
| Scalability | Good | Excellent | Good |
| Performance | Good | Excellent | Good |
| Reliability | Excellent | Excellent | Good |
| Features | Rich | Focused on streaming | Wide range |
| Community | Large | Large | Large |
| Ease of Use | Easy | Moderate | Moderate |
Real-World Applications of Messaging Queues
Messaging queues are used in a wide range of applications, including:
- E-commerce: Handling order processing, inventory management, and payment processing asynchronously to improve performance and responsiveness.
- Social Media: Managing real-time updates, notifications, and user interactions, ensuring scalability and reliability.
- Financial Services: Processing transactions, managing risk, and providing real-time data feeds for market analysis.
- Healthcare: Handling patient data, medical records, and scheduling appointments asynchronously to improve efficiency and security.
API Gateways: Top 10 Middleware Technologies
API gateways act as a central point of control for accessing and managing APIs. They provide a single entry point for external applications to interact with backend services, enhancing security, performance, and reliability.
Popular API Gateway Technologies
Popular API gateway technologies offer diverse features and capabilities.
- Kong: An open-source API gateway known for its flexibility and extensibility. It supports a wide range of plugins and integrations, enabling customization for specific needs.
- Tyk: Another open-source option, Tyk focuses on developer-friendly features and comprehensive analytics. It provides tools for API management, including documentation, testing, and monitoring.
- Apigee: A cloud-based API gateway platform, Apigee offers robust security features, advanced analytics, and integration with other Google Cloud services.
Enforcing Rate Limiting, Authentication, and Authorization
API gateways play a crucial role in enforcing security measures, including rate limiting, authentication, and authorization.
- Rate Limiting: API gateways can control the number of requests an application can make within a specific time frame, preventing excessive traffic and ensuring system stability. For example, a gateway can limit a user to making a maximum of 10 requests per minute.
- Authentication: API gateways verify the identity of clients attempting to access APIs. They can implement various authentication methods, such as API keys, OAuth, and JWT (JSON Web Token), to ensure only authorized users can access protected resources. For example, an API gateway can require a valid API key to be included in the request header before allowing access to a particular API.
- Authorization: API gateways control access to specific resources based on user roles and permissions. They can define policies that restrict access to certain APIs or endpoints based on user identity and privileges. For instance, an API gateway can allow only users with the “admin” role to access a specific endpoint that manages user accounts.
Service Buses
Service buses are a powerful middleware technology that simplifies communication between different services in a distributed system. They act as a central hub for message exchange, enabling services to interact with each other regardless of their underlying technology or location.
The Role of Service Buses
Service buses facilitate communication between services by providing a reliable and scalable mechanism for message exchange. They offer features like:
* Message Queues: Service buses use message queues to buffer messages, ensuring that even if a service is unavailable, messages are not lost. This enhances the reliability of communication.
* Message Routing: Service buses can intelligently route messages to the appropriate services based on predefined rules or patterns. This enables flexible and dynamic communication within a distributed system.
* Message Transformation: Service buses can transform messages between different formats, ensuring that services can communicate seamlessly even if they use different data structures or protocols.
* Message Security: Service buses can encrypt messages and implement authentication mechanisms to ensure secure communication between services.
Advantages of Using Service Buses
Service buses offer numerous advantages, including:
* Loose Coupling: Services communicate through messages, reducing direct dependencies between them. This allows for independent development and deployment of services, enhancing agility and flexibility.
* Scalability: Service buses can handle a high volume of messages, making them suitable for large-scale distributed systems. They can be easily scaled horizontally by adding more nodes to the bus.
* Reliability: Service buses ensure message delivery, even in the face of network failures or service outages. This guarantees that messages are processed, ensuring data consistency and preventing data loss.
* Centralized Management: Service buses provide a central point for managing and monitoring communication between services. This simplifies the administration and troubleshooting of the distributed system.
Disadvantages of Using Service Buses
While service buses offer significant advantages, they also have some drawbacks:
* Complexity: Implementing and managing a service bus can be complex, requiring specialized skills and knowledge.
* Performance Overhead: Service buses introduce additional layers of processing, which can impact performance, especially in high-throughput scenarios.
* Vendor Lock-in: Some service bus technologies can lead to vendor lock-in, making it difficult to switch to alternative solutions later.
Popular Service Bus Technologies
Several popular service bus technologies are available, each with its own strengths and weaknesses.
Apache Camel
* Apache Camel is a widely used open-source integration framework that provides a powerful and flexible service bus implementation.
* It supports a wide range of protocols and message formats, allowing for seamless integration between various services.
* Camel offers a rich set of components and connectors, making it easy to integrate with existing systems and applications.
* Apache Camel is known for its flexibility and extensibility, allowing developers to customize its behavior to meet specific requirements.
Mule ESB
* Mule ESB is another popular open-source enterprise service bus (ESB) platform.
* It provides a comprehensive set of features for building and managing enterprise-grade integrations.
* Mule ESB offers a visual development environment, making it easier to create and deploy integration flows.
* It also provides a range of connectors and adapters for integrating with various systems and applications.
WSO2
* WSO2 is a leading provider of open-source middleware solutions, including a robust service bus platform.
* WSO2’s service bus is highly scalable and reliable, making it suitable for large-scale enterprise deployments.
* It offers a comprehensive set of features for managing and monitoring service communication, including security, message routing, and transformation.
* WSO2 also provides a range of other middleware products, such as an API gateway, identity server, and data services platform, which can be integrated with its service bus.
Data Caching
Data caching is a technique used to store frequently accessed data in a temporary storage location, called a cache, to speed up data retrieval. This reduces the need to access the original data source, such as a database, which can be significantly slower.
Caching Strategies
Caching strategies are the rules and algorithms used to determine what data to cache, how long to keep it in the cache, and how to retrieve it. The choice of strategy depends on factors such as the type of data, the frequency of access, and the acceptable latency.
- Cache-aside: In this strategy, the application first checks the cache for the requested data. If the data is not found, it fetches it from the original source and stores it in the cache for future use. This is a common and straightforward approach, but it can introduce latency if the data is not found in the cache.
- Write-through: With write-through caching, every write operation is simultaneously performed on both the cache and the original data source. This ensures data consistency, but it can be slower than other strategies.
- Write-behind: In write-behind caching, write operations are first written to the cache and then asynchronously propagated to the original data source. This approach improves performance for write-intensive applications, but it can lead to data inconsistency if the cache fails before the data is written to the source.
- Read-through: This strategy is similar to cache-aside, but it always retrieves data from the original source, even if it is found in the cache. This ensures data consistency but can be slower.
Caching Technologies
Various caching technologies are available, each with its strengths and weaknesses.
- Redis: Redis is an open-source, in-memory data store that can be used for caching, messaging, and other purposes. It offers high performance, flexibility, and a wide range of data structures.
- Memcached: Memcached is another popular open-source in-memory caching system. It is known for its simplicity and high performance.
- Couchbase: Couchbase is a NoSQL database that can be used for both caching and data storage. It offers a combination of key-value storage, document database features, and a distributed architecture.
Comparison of Caching Technologies
| Feature | Redis | Memcached | Couchbase |
|---|---|---|---|
| Data Storage | In-memory | In-memory | In-memory and disk |
| Data Structures | Strings, lists, sets, sorted sets, hashes | Key-value pairs | Key-value pairs, documents |
| Persistence | Optional | No | Optional |
| Clustering | Yes | Yes | Yes |
| Scalability | High | High | High |
| Use Cases | Caching, messaging, session management | Caching, session management | Caching, data storage, NoSQL database |
Load Balancing
Load balancing is a crucial middleware technology that distributes incoming network traffic across multiple servers. It ensures that the workload is evenly distributed, preventing any single server from becoming overloaded and improving the overall performance and availability of the application. Load balancing acts as a traffic manager, directing requests to the most appropriate server based on various factors such as server availability, load, and specific application requirements.
Load Balancing Algorithms
Load balancing algorithms play a vital role in determining how traffic is distributed among servers. These algorithms ensure that the load is balanced effectively, maximizing system performance and availability.
Different load balancing algorithms have distinct characteristics and suit different scenarios. The choice of algorithm depends on factors such as the nature of the application, the expected traffic patterns, and the desired level of performance and reliability.
- Round Robin: This algorithm distributes requests to servers in a sequential, circular fashion. Each request is sent to the next server in the pool, ensuring that all servers receive an equal share of the traffic. Round Robin is a simple and efficient algorithm, but it does not consider server load or availability.
- Least Connections: This algorithm sends requests to the server with the fewest active connections. It aims to minimize the waiting time for incoming requests by directing them to servers with less workload. Least Connections is effective for applications with variable request processing times, but it can lead to uneven load distribution if servers have different processing capabilities.
- Weighted Round Robin: This algorithm is a variation of Round Robin that assigns weights to servers based on their capacity or processing power. Servers with higher weights receive a larger share of the traffic. Weighted Round Robin allows for more efficient load distribution by considering the server capabilities and ensuring that servers with higher capacity handle a greater workload.
- Random: This algorithm distributes requests to servers randomly. It is a simple and straightforward algorithm that can be effective in some scenarios, but it does not consider server load or availability. Random load balancing can lead to uneven load distribution, especially if servers have different processing capabilities.
- IP Hash: This algorithm uses the client’s IP address to determine the server that will handle the request. It ensures that requests from the same client are always routed to the same server. IP Hash is useful for maintaining session affinity, where a client’s session information needs to be preserved across multiple requests. However, it can lead to uneven load distribution if clients are not evenly distributed across the servers.
- Least Response Time: This algorithm selects the server with the shortest average response time to handle the request. It aims to minimize the overall response time for users by routing requests to servers that are currently responding quickly. Least Response Time is effective for applications with performance-critical operations, but it can lead to uneven load distribution if servers have different processing capabilities.
- Availability Zone: This algorithm ensures that requests are distributed across different availability zones, providing high availability and resilience. It avoids single points of failure by spreading the load across geographically diverse locations. Availability Zone load balancing is crucial for applications that require high availability and fault tolerance.
Popular Load Balancing Technologies
Several popular load balancing technologies are available, each with its strengths and weaknesses. The choice of technology depends on factors such as the size and complexity of the application, the required performance and reliability, and the budget.
- Nginx: Nginx is a high-performance, open-source web server and reverse proxy that is widely used for load balancing. It is known for its efficiency, scalability, and ease of configuration. Nginx supports various load balancing algorithms, including Round Robin, Least Connections, and Weighted Round Robin. It also provides features such as health checks, session persistence, and SSL/TLS termination.
- HAProxy: HAProxy is another popular, open-source load balancer that is known for its high performance and reliability. It is often used in high-traffic environments and supports various load balancing algorithms, including Round Robin, Least Connections, and Weighted Round Robin. HAProxy also offers features such as health checks, session persistence, and SSL/TLS termination.
- Apache Traffic Server: Apache Traffic Server is a high-performance, open-source HTTP caching and load balancing server. It is designed for high-volume web traffic and supports various load balancing algorithms, including Round Robin, Least Connections, and Weighted Round Robin. Apache Traffic Server also offers features such as caching, content delivery, and security.
Security Middleware

In today’s digital landscape, where applications are constantly under attack, security middleware plays a crucial role in safeguarding sensitive data and ensuring the integrity of applications. Security middleware acts as a protective shield, implementing various security mechanisms to protect applications from threats.
Authentication and Authorization
Authentication and authorization are fundamental aspects of security middleware, ensuring that only authorized users can access specific resources.
Authentication verifies the identity of users, typically through login credentials such as usernames and passwords. This process confirms that the user is who they claim to be.
Authorization, on the other hand, determines what actions a user is permitted to perform once authenticated. It defines access rights and privileges based on user roles or group memberships.
Encryption, Top 10 middleware technologies
Encryption is a vital security measure that transforms data into an unreadable format, preventing unauthorized access. Security middleware utilizes encryption algorithms to protect sensitive data during transmission and storage.
Data encryption can be implemented at various levels, including:
– Transport Layer Security (TLS): TLS encrypts data exchanged between the client and server, ensuring secure communication over the internet.
– Data at Rest: Encrypting data stored in databases or files safeguards it from unauthorized access even if the system is compromised.
Popular Security Middleware Technologies
Security middleware encompasses a wide range of technologies, each offering unique features and benefits.
- OAuth: OAuth is an open standard for delegated authorization, allowing users to grant third-party applications access to their data without sharing their credentials. It focuses on authorization and provides a mechanism for secure delegation of access.
- OpenID Connect: OpenID Connect builds upon OAuth and provides an authentication layer, enabling users to log in to multiple applications using a single identity provider. It provides a standardized framework for authentication and authorization.
- Spring Security: Spring Security is a comprehensive security framework for Java applications. It offers a wide range of features, including authentication, authorization, access control, and encryption. It provides a robust and flexible solution for securing Java applications.
Monitoring and Logging
In the dynamic world of software applications, understanding the health and behavior of your systems is paramount. Monitoring and logging middleware play a crucial role in providing valuable insights into the performance, errors, and security events that occur within your applications. By effectively tracking and analyzing this data, you can proactively identify and resolve issues, optimize performance, and ensure the security of your applications.
Popular Monitoring and Logging Technologies
These technologies provide a comprehensive view of your application’s health, allowing you to make informed decisions and take appropriate actions.
- Prometheus: An open-source monitoring system that uses a time-series database to store and query metrics. It excels in its simplicity, scalability, and flexibility, allowing you to define custom metrics and dashboards to monitor your applications.
- Grafana: A powerful open-source platform for visualizing and analyzing data from various sources, including Prometheus. It provides interactive dashboards, alerts, and data exploration tools, making it easy to understand and interpret your monitoring data.
- ELK Stack: A popular open-source logging and analytics platform that consists of Elasticsearch, Logstash, and Kibana. Elasticsearch provides a highly scalable and performant search engine for storing and querying logs, Logstash allows you to process and transform logs, and Kibana offers a user-friendly interface for visualizing and analyzing log data.
Future Trends in Middleware
Middleware is constantly evolving to meet the demands of modern application development. The rise of cloud computing, the increasing popularity of microservices, and the need for faster and more efficient applications are driving innovation in the middleware space. As a result, several emerging trends are shaping the future of middleware development.
Serverless Computing
Serverless computing is a cloud computing execution model where the cloud provider dynamically manages the allocation of server resources. This allows developers to focus on writing code without worrying about managing servers or infrastructure. Serverless computing is becoming increasingly popular for middleware because it offers several advantages, including:
- Reduced Operational Overhead: Developers can focus on building applications without worrying about managing servers or infrastructure. This frees up time and resources for innovation.
- Scalability: Serverless functions can scale automatically based on demand, ensuring that applications can handle peak loads without performance degradation.
- Cost Efficiency: Developers only pay for the resources they use, which can lead to significant cost savings compared to traditional server-based deployments.
Serverless middleware platforms are emerging that provide a range of services, including messaging queues, API gateways, and data caching. These platforms are designed to be highly scalable, cost-effective, and easy to use.
Edge Computing
Edge computing is a distributed computing paradigm that brings computation and data storage closer to the source of data. This can improve application performance, reduce latency, and enhance data privacy. Edge computing is becoming increasingly important for middleware as applications become more distributed and data is generated at the edge of the network.
Edge computing is particularly relevant for middleware technologies like:
- Content Delivery Networks (CDNs): Edge computing enables CDNs to deliver content faster and more efficiently to users around the world.
- Internet of Things (IoT): Edge computing is essential for processing data from IoT devices in real time, reducing latency and enabling faster decision-making.
- Real-Time Analytics: Edge computing allows for real-time analysis of data generated at the edge of the network, enabling faster insights and decision-making.
Edge computing middleware platforms are emerging that provide a range of services, including data storage, processing, and analytics. These platforms are designed to be highly scalable, secure, and resilient.
Microservices
Microservices are a software development approach that structures an application as a collection of loosely coupled services. Each service is responsible for a specific business capability and can be developed, deployed, and scaled independently. Microservices are becoming increasingly popular because they offer several advantages, including:
- Improved Agility: Teams can work independently on different services, leading to faster development cycles and increased agility.
- Enhanced Scalability: Services can be scaled independently based on demand, ensuring that applications can handle peak loads without performance degradation.
- Increased Resilience: The failure of one service does not affect the entire application, making applications more resilient to failures.
Microservices architecture requires middleware to manage communication between services and ensure data consistency. Middleware technologies like messaging queues, API gateways, and service buses are essential for enabling microservices communication and coordination.
Last Recap
As the world of software development continues to evolve, middleware technologies will play an increasingly critical role in shaping the future of applications. By embracing these powerful tools, developers can build innovative solutions that meet the ever-growing demands of the digital landscape.
Top 10 middleware technologies encompass a wide range of solutions, from message queues to API gateways. These technologies play a crucial role in connecting different systems and applications, enabling seamless data flow and efficient communication. In a similar vein, understanding what features are included in a technology package on a car like the Acura MDX can be just as important.
For instance, you might be interested in learning more about what is technology package on acura mdx , as it could influence your decision on whether to purchase the vehicle. Ultimately, both middleware technologies and car technology packages aim to enhance user experience by providing essential features and functionalities.