Technology Due Diligence Checklist: A Guide for Mergers and Acquisitions
The Technology Due Diligence Checklist is an essential tool for any company considering a merger or acquisition. It helps to identify potential risks and opportunities related to the target company’s […]
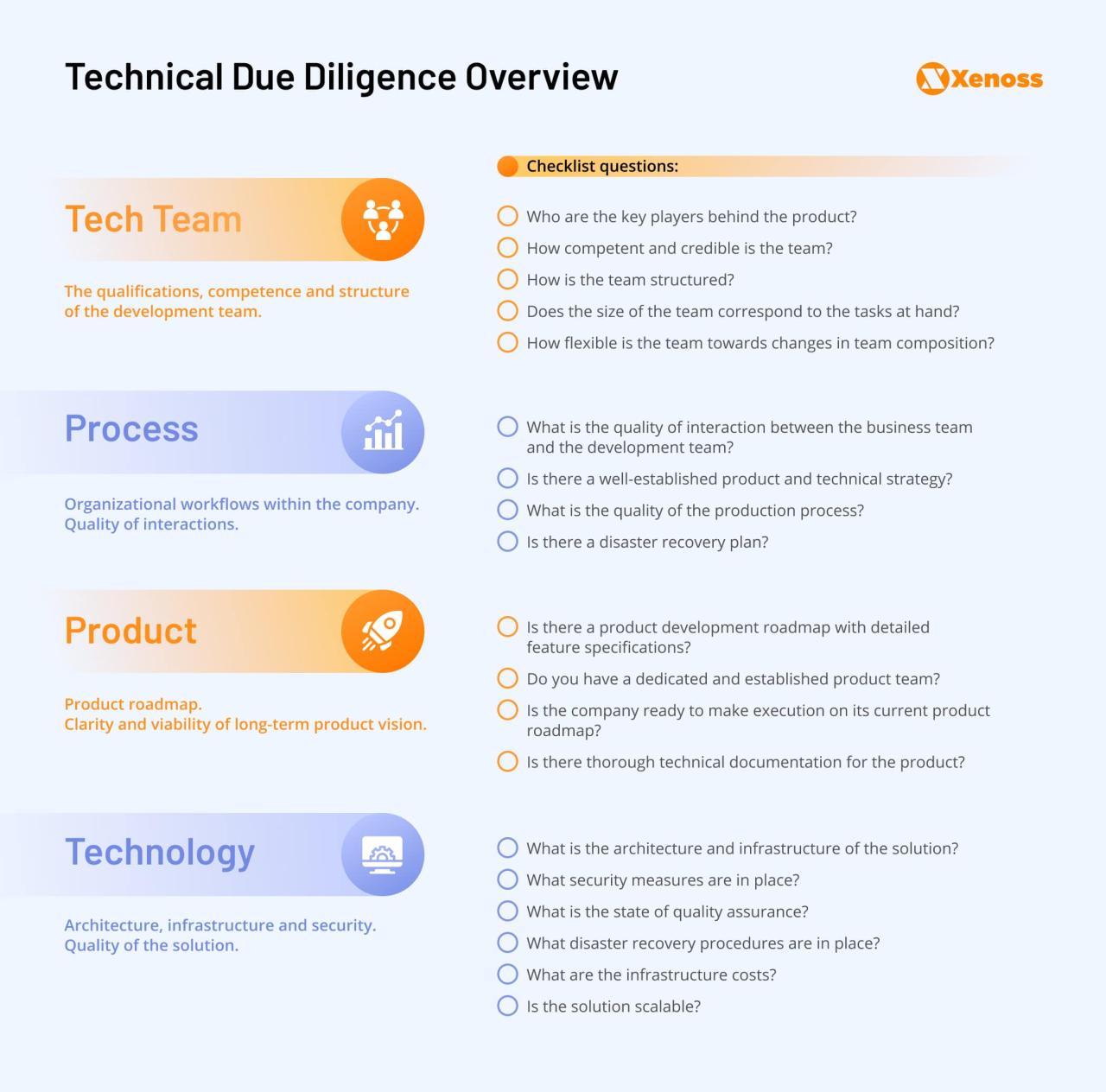
The Technology Due Diligence Checklist is an essential tool for any company considering a merger or acquisition. It helps to identify potential risks and opportunities related to the target company’s technology infrastructure, software, data, cybersecurity, and more. This checklist is crucial for ensuring a smooth transition and mitigating potential post-acquisition challenges.
By thoroughly evaluating the target company’s technology landscape, acquirers can gain valuable insights into the potential impact of the acquisition on their own operations. This includes understanding the target company’s technology capabilities, identifying any potential integration issues, and assessing the overall financial implications of the deal.
Data Management

Data management practices are crucial for any technology company, particularly during due diligence. This section examines the target company’s data management practices, focusing on data security, privacy, and compliance, as well as data backup and recovery procedures, including data retention policies. Additionally, it evaluates data migration strategies and potential challenges in integrating data systems.
Data Security, Privacy, and Compliance
Data security, privacy, and compliance are essential aspects of data management. Understanding the target company’s approach to these areas is crucial.
- Data Security Measures: Analyze the security measures implemented to protect sensitive data. This includes encryption methods, access controls, and security protocols.
- Privacy Policies: Evaluate the target company’s privacy policies and compliance with relevant regulations, such as GDPR (General Data Protection Regulation) or CCPA (California Consumer Privacy Act).
- Compliance Audits: Determine the frequency and scope of compliance audits conducted to ensure adherence to data security and privacy standards.
- Incident Response Plan: Assess the company’s incident response plan for data breaches and security incidents.
Data Backup and Recovery Procedures
Data backup and recovery procedures are critical for business continuity and disaster recovery.
- Backup Frequency and Methods: Determine the frequency and methods of data backups, including the types of data backed up (e.g., databases, files, applications).
- Data Retention Policies: Analyze the company’s data retention policies, ensuring they comply with legal and regulatory requirements.
- Disaster Recovery Plan: Evaluate the disaster recovery plan, including the procedures for restoring data and systems in case of a major disruption.
Data Migration Strategies
Data migration is a crucial aspect of integrating data systems during an acquisition or merger.
- Migration Plan: Review the data migration plan, including the scope, timeline, and resources allocated.
- Data Conversion and Transformation: Analyze the processes for data conversion and transformation to ensure compatibility with the acquiring company’s systems.
- Potential Challenges: Identify potential challenges in data migration, such as data quality issues, system compatibility problems, and data loss risks.
Cybersecurity
Cybersecurity is a critical aspect of due diligence, especially in today’s digital world. It is crucial to understand the target company’s cybersecurity posture to identify potential risks and vulnerabilities that could impact the deal. This section focuses on evaluating the target company’s cybersecurity practices and their alignment with industry best practices and regulations.
Cybersecurity Risk Assessment
A thorough cybersecurity risk assessment helps identify potential threats and vulnerabilities. It involves analyzing the target company’s IT infrastructure, systems, and data to determine the likelihood and impact of various cyberattacks.
- Identify potential threats: This involves understanding the specific threats that the target company might face, such as malware, phishing attacks, ransomware, and denial-of-service attacks.
- Assess vulnerabilities: This involves evaluating the target company’s systems and networks for weaknesses that could be exploited by attackers. For example, outdated software, weak passwords, and misconfigured firewalls can create vulnerabilities.
- Analyze the impact of potential threats: This involves assessing the potential consequences of a successful cyberattack, such as data breaches, financial losses, reputational damage, and operational disruptions.
Security Controls and Policies
Evaluating the target company’s security controls and policies is essential to understand how they mitigate identified risks. This involves examining their existing security framework, including policies, procedures, and technologies.
- Access control: This involves evaluating the target company’s access control measures, such as user authentication, authorization, and role-based access control.
- Data security: This involves assessing the target company’s data security practices, including data encryption, data backups, and data loss prevention measures.
- Network security: This involves evaluating the target company’s network security measures, such as firewalls, intrusion detection systems, and network segmentation.
- Endpoint security: This involves assessing the target company’s endpoint security measures, such as antivirus software, endpoint detection and response (EDR) solutions, and device management policies.
- Security awareness training: This involves evaluating the target company’s security awareness training programs, which aim to educate employees about cybersecurity risks and best practices.
Incident Response
A robust incident response plan is crucial for handling cybersecurity incidents effectively. It Artikels the steps to be taken in the event of a security breach, including containment, investigation, remediation, and recovery.
- Incident detection: This involves evaluating the target company’s systems and processes for detecting security incidents, such as intrusion detection systems, security monitoring tools, and employee reporting mechanisms.
- Incident response procedures: This involves reviewing the target company’s incident response procedures, including the roles and responsibilities of key personnel, communication protocols, and escalation procedures.
- Incident recovery: This involves assessing the target company’s ability to recover from a security incident, including data restoration, system recovery, and business continuity plans.
Compliance with Regulations and Best Practices
The target company should comply with relevant cybersecurity regulations and industry best practices. This demonstrates their commitment to responsible cybersecurity practices and reduces the risk of legal and financial penalties.
- General Data Protection Regulation (GDPR): This regulation applies to companies that process personal data of individuals in the European Union. It requires companies to implement appropriate technical and organizational measures to protect personal data.
- California Consumer Privacy Act (CCPA): This law applies to companies that collect, use, or disclose personal information of California residents. It requires companies to provide consumers with certain rights regarding their data, such as the right to access, delete, and opt-out of the sale of their data.
- Payment Card Industry Data Security Standard (PCI DSS): This standard applies to companies that process, store, or transmit credit card data. It requires companies to implement security measures to protect cardholder data.
- NIST Cybersecurity Framework: This framework provides a set of guidelines for organizations to manage cybersecurity risks. It covers five core functions: identify, protect, detect, respond, and recover.
Cybersecurity Due Diligence Considerations
The following considerations are essential during the cybersecurity due diligence process:
- Obtain relevant documentation: This includes security policies, procedures, incident response plans, vulnerability assessments, penetration test reports, and audit reports.
- Interview key personnel: This includes the Chief Information Security Officer (CISO), security engineers, and other relevant personnel.
- Conduct a technical assessment: This may involve conducting a vulnerability scan, penetration test, or other technical assessments to identify security weaknesses.
- Assess the target company’s cybersecurity culture: This involves understanding the target company’s commitment to cybersecurity and the level of awareness and training among employees.
Technology Talent
The technology talent of the target company is a crucial factor in determining the success of an acquisition. A strong technology team can ensure a smooth integration process, maintain existing systems, and drive future innovation.
Skills and Experience
This section explores the skills and experience of the target company’s technology team. It assesses the team’s capabilities in areas relevant to the acquirer’s goals.
- Technical Expertise: Assess the team’s expertise in the relevant technologies, including programming languages, frameworks, and platforms. Consider the team’s experience in areas such as cloud computing, data analytics, artificial intelligence, and cybersecurity.
- Domain Knowledge: Evaluate the team’s understanding of the target company’s industry and business processes. This knowledge is essential for ensuring the smooth integration of technology systems and supporting the business needs.
- Project Management: Assess the team’s experience in managing technology projects, including planning, execution, and delivery. This includes understanding project methodologies, risk management, and communication skills.
Team Structure and Roles
This section delves into the structure, roles, and responsibilities of the target company’s technology team. It helps understand the team’s organization and how it operates.
- Team Size and Structure: Determine the size of the technology team and its organizational structure. Understand the reporting lines and how the team is divided into different functional areas.
- Roles and Responsibilities: Identify the key roles within the team, such as software engineers, data analysts, cybersecurity specialists, and IT infrastructure managers. Assess the responsibilities associated with each role and the team’s overall workflow.
- Communication and Collaboration: Evaluate the team’s communication and collaboration practices. This includes understanding the use of tools, processes, and team dynamics.
Retention of Key Personnel
This section focuses on the potential for retaining key technology personnel after the acquisition. This is essential for maintaining the target company’s technological capabilities and ensuring a smooth transition.
- Key Personnel Identification: Identify the key technology personnel who are essential for the target company’s operations. This includes individuals with specialized skills, deep domain knowledge, or leadership roles.
- Retention Strategies: Develop retention strategies to keep these key individuals engaged and motivated. This may involve offering competitive compensation packages, providing career growth opportunities, and fostering a positive work environment.
- Integration Planning: Plan for the integration of the technology team into the acquirer’s organization. This includes addressing concerns about job security, career paths, and cultural differences.
Technology Strategy: Technology Due Diligence Checklist
A thorough analysis of the target company’s technology strategy is crucial for understanding its future direction and the potential impact of the acquisition. This section examines the technology roadmap, investment plans, and alignment with business objectives.
Technology Roadmap and Future Investment Plans
The technology roadmap Artikels the target company’s planned technology investments and initiatives over a specific period. It provides insights into the company’s strategic direction and its commitment to innovation. Evaluating the technology roadmap allows us to assess the target company’s ability to adapt to changing market conditions and stay ahead of the competition.
- Timeline and Milestones: The roadmap should clearly define the timeline for key technology initiatives and the expected milestones. This information helps us understand the company’s progress and its ability to execute its plans.
- Investment Allocation: Analyzing the investment allocation across different technology areas reveals the company’s priorities and its commitment to specific technologies. For example, a significant investment in cloud computing suggests a focus on agility and scalability.
- Alignment with Business Objectives: The technology roadmap should be closely aligned with the company’s overall business objectives. For instance, if the company aims to expand into new markets, the technology roadmap should include initiatives that support this expansion.
Alignment with Business Objectives
The technology strategy should be aligned with the overall business objectives. This means that technology investments and initiatives should support the company’s strategic goals and contribute to its long-term success. For example, a company aiming to increase efficiency and reduce costs might invest in automation and process optimization technologies.
- Strategic Goals: Understanding the target company’s strategic goals helps us assess the alignment of the technology strategy. For example, if the company aims to achieve market leadership, its technology investments should focus on innovation and differentiation.
- Key Performance Indicators (KPIs): The technology strategy should be aligned with key performance indicators (KPIs) that measure the company’s success. For example, if the company aims to improve customer satisfaction, its technology investments should focus on enhancing customer experience.
- Risk Management: The technology strategy should address potential risks and challenges that could impact the company’s business objectives. For example, a company operating in a highly regulated industry might need to invest in cybersecurity and compliance technologies.
Potential Impact of the Acquisition
The acquisition can have a significant impact on the target company’s technology strategy. For example, the acquiring company might have a different technology platform or a different approach to technology investments. It’s crucial to evaluate the potential impact of the acquisition on the target company’s technology strategy and to develop a plan for integrating the two organizations’ technology systems.
- Integration Challenges: Integrating the target company’s technology systems with the acquiring company’s systems can be complex and time-consuming. It’s essential to identify potential integration challenges and develop a plan for addressing them.
- Technology Synergies: The acquisition might create opportunities for technology synergies. For example, the acquiring company might have expertise in a specific technology area that could benefit the target company.
- Future Technology Investments: The acquisition might influence the target company’s future technology investments. For example, the acquiring company might have a different vision for the target company’s technology roadmap.
Conclusion
This technology due diligence review has assessed the target company’s technology landscape across several key areas, including data management, cybersecurity, technology talent, and technology strategy. The review has identified both strengths and areas for improvement, providing valuable insights for decision-making.
Key Findings and Recommendations, Technology due diligence checklist
The technology due diligence has revealed several key findings, highlighting both potential risks and opportunities. These findings can be categorized as follows:
- Data Management: The target company has implemented robust data management practices, including data governance, data quality, and data security measures. However, there is an opportunity to enhance data analytics capabilities to extract greater insights from the company’s data assets.
- Cybersecurity: The target company has a strong cybersecurity posture with comprehensive security controls and incident response procedures. However, it is recommended to continuously monitor emerging threats and vulnerabilities and adapt security measures accordingly.
- Technology Talent: The target company boasts a skilled and experienced technology team, demonstrating expertise in various technologies. However, it is crucial to ensure that the team has access to ongoing training and development opportunities to stay abreast of industry advancements.
- Technology Strategy: The target company has a well-defined technology strategy aligned with its business objectives. However, it is recommended to regularly review and update the strategy to ensure it remains relevant in a rapidly evolving technological landscape.
End of Discussion
A comprehensive technology due diligence checklist provides a clear picture of the target company’s technology landscape. It allows acquirers to make informed decisions about the acquisition, identify potential risks and opportunities, and develop strategies for integrating the target company’s technology into their own operations. By taking the time to thoroughly assess the target company’s technology, acquirers can minimize the risk of unexpected surprises and ensure a successful integration.
A technology due diligence checklist should include an assessment of the vendor’s technical capabilities and the maturity of their solutions. For example, when considering a mattress like the Sealy Performance Posturepedic Technology King , you’d want to understand the materials used and how they contribute to the overall comfort and support.
This type of investigation ensures that the technology being implemented aligns with your business needs and objectives.