Technology Assigned Risk: Understanding and Managing IT Threats
Technology assigned risk, a critical aspect of modern business operations, involves identifying and mitigating the potential threats posed by technology failures or vulnerabilities. This intricate interplay of risk assessment and […]
Technology assigned risk, a critical aspect of modern business operations, involves identifying and mitigating the potential threats posed by technology failures or vulnerabilities. This intricate interplay of risk assessment and technology management ensures that businesses can thrive in an increasingly digital world, while safeguarding their assets and reputation.
The concept of technology assigned risk extends beyond mere technical considerations, encompassing a holistic approach that examines the impact of technology on various business aspects, including financial stability, operational efficiency, and brand image. By understanding the specific risks associated with each technology system and implementing appropriate safeguards, businesses can effectively minimize potential losses and optimize their technology investments.
Defining Technology Assigned Risk
Technology assigned risk is a type of risk that arises from the use of technology within an organization. It’s essentially the potential for negative consequences that can stem from technological failures, vulnerabilities, or misuse.
Technology Assigned Risk Compared to Other Risk Categories
Technology assigned risk can be categorized alongside other types of risk, but it has distinct characteristics. Here’s a comparison:
- Operational Risk: This encompasses risks related to day-to-day business operations, including technology. Technology assigned risk is a subset of operational risk, specifically focusing on the technology aspect.
- Financial Risk: This pertains to risks associated with financial performance, like market fluctuations or credit risk. Technology assigned risk can indirectly impact financial risk, for instance, through data breaches leading to financial losses.
- Strategic Risk: This category deals with risks related to an organization’s long-term goals and strategy. Technology assigned risk can be a strategic risk if, for example, a company’s reliance on outdated technology hinders its ability to adapt to market changes.
Importance of Understanding Technology Assigned Risk
Understanding technology assigned risk is crucial for organizations as it allows them to:
- Identify and Mitigate Potential Threats: By recognizing the specific risks associated with their technology infrastructure, organizations can implement appropriate security measures, update software regularly, and train employees on safe practices to minimize the impact of potential threats.
- Optimize Business Operations: Technology assigned risk assessment can reveal vulnerabilities in processes and systems that hinder efficiency. By addressing these issues, organizations can improve their operational performance and achieve better outcomes.
- Make Informed Decisions: Understanding the risks associated with technology investments helps organizations make more informed decisions about technology adoption, ensuring that the chosen technologies align with their risk tolerance and strategic objectives.
- Enhance Competitive Advantage: Organizations that proactively manage technology assigned risk can gain a competitive edge by demonstrating a strong commitment to data security, operational efficiency, and technological innovation.
Identifying Technology Assigned Risks

Identifying technology assigned risks is a critical step in managing technology-related risks. This involves understanding the potential threats, vulnerabilities, and impacts that could arise from technology within an organization. A comprehensive assessment helps to prioritize mitigation strategies and ensure business continuity.
Common Technology Assigned Risks
The following is a list of common technology assigned risks that organizations may face:
- Data breaches and security incidents
- System failures and downtime
- Cyberattacks, including ransomware and phishing
- Software vulnerabilities and bugs
- Hardware failures and malfunctions
- Loss of data integrity and availability
- Compliance violations and regulatory fines
- Disruptions to business operations
- Reputation damage and loss of customer trust
- Financial losses due to fraud or theft
- Unforeseen technology obsolescence
- Inadequate IT infrastructure and capacity
- Lack of skilled IT personnel
- Poor technology governance and risk management practices
Categorization of Technology Assigned Risks
To better understand the impact of technology assigned risks, they can be categorized based on their potential consequences:
| Risk Category | Impact | Example | Mitigation Strategy |
|---|---|---|---|
| Financial | Financial losses, including revenue loss, increased costs, and fines | Data breach leading to financial fraud and theft | Strong data encryption, secure payment gateways, and fraud detection systems |
| Operational | Disruptions to business operations, delays in production, and service outages | System failure causing website downtime and customer service disruptions | Redundant systems, disaster recovery plans, and robust system monitoring |
| Reputational | Damage to brand reputation, loss of customer trust, and negative media coverage | Cyberattack exposing sensitive customer data, leading to public distrust | Strong security measures, incident response plans, and transparent communication |
| Legal and Regulatory | Compliance violations, legal penalties, and regulatory fines | Failure to comply with data privacy regulations, leading to legal action | Data privacy compliance programs, regular audits, and legal counsel |
Factors Contributing to Risk Severity and Likelihood
Several factors contribute to the severity and likelihood of technology assigned risks, including:
- Complexity of technology: More complex systems are often more vulnerable to errors and attacks.
- Dependence on technology: Organizations heavily reliant on technology are more susceptible to disruptions.
- Security posture: Weak security controls and practices increase the risk of breaches and attacks.
- External threats: Cybercriminals, natural disasters, and geopolitical events can pose significant threats.
- Internal factors: Human error, lack of training, and inadequate risk management practices can contribute to risks.
Managing Technology Assigned Risks
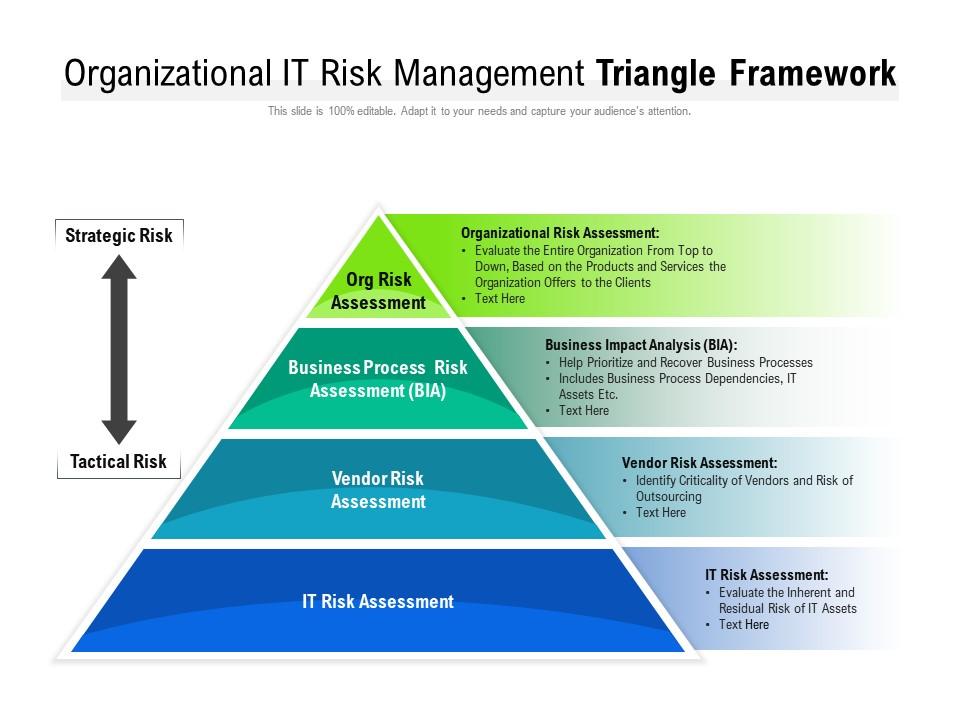
Once you have identified and assessed technology assigned risks, the next step is to manage them effectively. This involves developing a comprehensive framework that Artikels strategies for mitigating, controlling, and monitoring these risks.
A Framework for Managing Technology Assigned Risks
A robust framework for managing technology assigned risks should incorporate the following key elements:
- Risk Acceptance: This involves acknowledging that some risks are unavoidable or too costly to mitigate completely. For example, a company may accept the risk of a minor data breach if the cost of implementing stronger security measures is deemed excessive.
- Risk Avoidance: This strategy involves completely avoiding certain risks by altering or eliminating the activity or technology associated with them. For instance, a company might decide to avoid using a particular cloud service if it poses a significant security risk.
- Risk Mitigation: This involves taking steps to reduce the likelihood or impact of a risk. Examples include implementing stronger security measures, conducting regular vulnerability scans, and providing employee training on cybersecurity best practices.
- Risk Transfer: This involves transferring the risk to a third party, such as an insurance company or a service provider. For example, a company might purchase cyber liability insurance to protect itself from financial losses in the event of a data breach.
- Risk Monitoring: This involves continuously tracking the effectiveness of risk management strategies and making adjustments as needed. This can be done through regular risk assessments, performance audits, and incident reporting.
Best Practices for Mitigating Technology Assigned Risks
- Establish a Strong Security Posture: Implement robust security measures, including firewalls, intrusion detection systems, and multi-factor authentication, to protect against unauthorized access and cyberattacks. Regularly update software and systems to patch vulnerabilities.
- Promote a Culture of Cybersecurity: Encourage employees to follow best practices, such as using strong passwords, being cautious about phishing emails, and reporting suspicious activity. Provide regular cybersecurity training to raise awareness and build skills.
- Conduct Regular Risk Assessments: Regularly evaluate the effectiveness of risk management strategies and identify new or emerging risks. This involves analyzing potential threats, vulnerabilities, and impacts.
- Implement a Data Loss Prevention Strategy: Establish measures to prevent sensitive data from being lost or stolen, such as data encryption, access control, and data backups. Conduct regular data audits to ensure compliance with regulations.
- Leverage Technology Solutions: Utilize advanced technologies such as artificial intelligence (AI) and machine learning (ML) to detect and respond to threats in real time. Implement threat intelligence platforms to stay ahead of emerging cyberattacks.
Implementing Risk Assessment and Control Measures
- Define the Scope of the Assessment: Clearly identify the technology assets, processes, and data that will be included in the risk assessment. This should be aligned with the company’s overall risk appetite and strategic objectives.
- Identify Potential Threats and Vulnerabilities: Conduct a comprehensive analysis of potential threats, including cyberattacks, natural disasters, human error, and technical failures. Identify vulnerabilities in systems, applications, and infrastructure that could be exploited by these threats.
- Assess the Likelihood and Impact of Risks: Estimate the probability of each risk occurring and the potential impact on the organization. This can be done using qualitative or quantitative methods, depending on the complexity of the risks.
- Develop Control Measures: Design and implement control measures to mitigate the identified risks. These measures should be tailored to the specific nature of each risk and should be cost-effective and practical to implement.
- Monitor and Evaluate Control Measures: Regularly review and evaluate the effectiveness of control measures. Make adjustments as needed to ensure they remain effective in mitigating risks.
Technology Assigned Risk in Different Industries
Technology assigned risk is a critical aspect of managing technology in any industry. It involves identifying, assessing, and mitigating potential risks associated with the use and implementation of technology. The specific risks faced by different industries vary significantly due to their unique operating environments, regulatory landscapes, and technological requirements. Understanding these industry-specific risks is crucial for effective risk management and ensuring the successful adoption of technology.
Technology Assigned Risks in Different Industries
The following table Artikels the key technology assigned risks faced by different industries:
| Industry | Technology Assigned Risks | Examples | Management Strategies |
|---|---|---|---|
| Healthcare | Data breaches, cyberattacks, patient privacy violations, HIPAA compliance, system downtime, medical device malfunctions, interoperability issues | – Hackers gaining access to sensitive patient data, leading to identity theft or financial fraud. – System downtime during critical procedures, resulting in delays or compromised patient care. – Medical devices malfunctioning, causing harm to patients or inaccurate diagnoses. |
– Implementing robust cybersecurity measures, such as firewalls, intrusion detection systems, and encryption. – Training healthcare professionals on data privacy and security best practices. – Conducting regular security audits and vulnerability assessments. – Establishing disaster recovery plans to minimize downtime. |
| Finance | Fraudulent transactions, cyberattacks, data breaches, regulatory compliance, system outages, market volatility, financial modeling errors | – Hackers stealing customer financial information, leading to unauthorized transactions. – System outages disrupting trading activities, causing financial losses. – Financial modeling errors resulting in inaccurate risk assessments or investment decisions. |
– Implementing strong authentication measures, such as multi-factor authentication. – Using advanced fraud detection systems to identify and prevent suspicious activities. – Ensuring compliance with relevant financial regulations, such as Dodd-Frank and GDPR. – Regularly testing and updating financial models to mitigate errors. |
| Manufacturing | Cyberattacks, production disruptions, equipment failures, supply chain disruptions, data security breaches, automation risks | – Hackers compromising manufacturing systems, leading to production delays or shutdowns. – Equipment failures causing production bottlenecks or product defects. – Supply chain disruptions due to natural disasters or cyberattacks. |
– Implementing robust cybersecurity measures to protect manufacturing systems. – Conducting regular equipment maintenance and inspections to prevent failures. – Diversifying supply chains to mitigate disruptions. – Utilizing data analytics to identify and address potential risks. |
Methods for Managing Technology Assigned Risks
The methods for managing technology assigned risks vary across different industries. Some common strategies include:
– Risk Assessment: This involves identifying, analyzing, and prioritizing potential risks based on their likelihood and impact.
– Risk Mitigation: Implementing measures to reduce the likelihood or impact of identified risks.
– Risk Transfer: Transferring the risk to a third party, such as through insurance or outsourcing.
– Risk Acceptance: Accepting the risk and taking no action, which may be appropriate for low-impact risks.
– Contingency Planning: Developing plans to address potential risks and ensure business continuity.
While the specific risks and management strategies may differ, the overall goal is to minimize the impact of technology assigned risks and ensure the successful adoption of technology in each industry.
The Future of Technology Assigned Risk
The landscape of technology assigned risk is constantly evolving, driven by the rapid pace of technological advancements and the increasing reliance on technology in all aspects of life. As technology becomes more sophisticated and interconnected, the potential for both positive and negative impacts on risk management is growing.
Emerging Trends and Challenges
Emerging trends and challenges in technology assigned risk are constantly shaping the way organizations approach risk management. These trends and challenges create a dynamic environment that requires organizations to be agile and adaptable.
- Increased Complexity of Technology: The increasing complexity of technology, such as artificial intelligence (AI), blockchain, and the Internet of Things (IoT), is creating new risks that organizations need to understand and manage. This complexity can make it difficult to identify, assess, and mitigate risks effectively.
- Cybersecurity Threats: The rise of sophisticated cyberattacks and data breaches is a major concern for organizations. These threats can disrupt operations, damage reputation, and lead to significant financial losses. Organizations need to invest in robust cybersecurity measures to protect their systems and data.
- Data Privacy and Security: The increasing amount of data being collected and stored by organizations is raising concerns about data privacy and security. Organizations need to comply with data privacy regulations and ensure that they are protecting sensitive information.
- Regulatory Changes: Governments and regulatory bodies are constantly evolving their regulations to keep pace with technological advancements. Organizations need to stay informed about these changes and ensure that they are in compliance.
- Emerging Technologies: The rapid development of new technologies, such as quantum computing and gene editing, presents both opportunities and risks. Organizations need to assess the potential impact of these technologies on their operations and risk profiles.
Impact of Technological Advancements
Technological advancements have a significant impact on technology assigned risk, both in terms of creating new risks and providing opportunities to manage risks more effectively.
- AI and Machine Learning: AI and machine learning can be used to automate risk assessment and mitigation processes, making them more efficient and accurate. However, these technologies also introduce new risks, such as the potential for bias and errors in decision-making.
- Cloud Computing: Cloud computing offers organizations flexibility and scalability, but it also raises concerns about data security and compliance. Organizations need to ensure that their cloud providers have adequate security measures in place.
- Blockchain Technology: Blockchain technology can improve transparency and security in supply chains and other processes. However, it also presents challenges in terms of scalability and regulatory compliance.
- IoT: The widespread adoption of IoT devices is creating new opportunities for organizations to collect data and improve efficiency. However, it also increases the attack surface for cybercriminals.
Timeline of Technology Assigned Risk Management
The future of technology assigned risk management is likely to be shaped by the ongoing evolution of technology and the increasing importance of risk management in a digital world.
- Short-Term (Next 5 Years):
- Increased focus on cybersecurity and data privacy.
- Widespread adoption of AI and machine learning for risk management.
- Growing use of cloud computing and blockchain technology.
- Mid-Term (Next 10-15 Years):
- Emergence of new technologies, such as quantum computing and gene editing, will create new risks and opportunities.
- Greater reliance on automation and artificial intelligence in risk management.
- Increased regulation of technology and data privacy.
- Long-Term (Beyond 15 Years):
- Technology assigned risk management will become increasingly integrated with other business functions.
- Organizations will need to be highly agile and adaptable to respond to rapidly changing technology and risk landscapes.
- The role of risk managers will evolve to include a greater focus on emerging technologies and their potential impact on business operations.
Outcome Summary
Successfully navigating the ever-evolving landscape of technology requires a proactive and strategic approach to managing technology assigned risk. By embracing a comprehensive framework that incorporates risk assessment, mitigation strategies, and ongoing monitoring, businesses can build resilience, enhance operational efficiency, and foster a culture of responsible technology utilization. As technology continues to transform the business landscape, embracing technology assigned risk management is not merely an option, but a necessity for long-term success.
Technology assigned risk is a crucial aspect of evaluating the potential downsides of new innovations. This is especially true in the field of healthcare, where patient safety is paramount. A great example is the emergence of new technology dental braces , which offer faster treatment times and greater comfort.
However, their long-term effectiveness and potential complications require careful assessment before widespread adoption. This highlights the importance of thorough risk analysis in the development and implementation of any new technological solution.