SIM Technology: Connecting the World
SIM technology, the unsung hero of mobile communication, has quietly revolutionized how we connect and interact with the world. From the humble beginnings of bulky SIM cards to the sleek […]
SIM technology, the unsung hero of mobile communication, has quietly revolutionized how we connect and interact with the world. From the humble beginnings of bulky SIM cards to the sleek and invisible eSIMs of today, this technology has evolved alongside our mobile lives, enabling seamless communication, secure transactions, and a plethora of innovative applications.
SIM cards, those tiny chips tucked away in our phones, hold the key to our mobile identities. They store our personal information, authentication credentials, and even our mobile payment details. This seemingly simple piece of technology is the cornerstone of a vast and intricate network that allows us to stay connected, access information, and engage in a digital world.
Introduction to SIM Technology

The Subscriber Identity Module (SIM) is a small, removable chip that stores essential information about a mobile phone user. It acts as the user’s identity within a mobile network, enabling them to make calls, send messages, and access data services. The SIM card has played a pivotal role in the evolution of mobile communication, evolving from a relatively simple device to a complex component with advanced capabilities.
History and Evolution of SIM Cards
The SIM card’s history dates back to the early days of mobile communication. The first generation of mobile phones (1G) used a system called “analog cellular,” which required a physical connection to the network through a base station. This system lacked the flexibility and portability that we enjoy today.
In the 1990s, the introduction of the second generation (2G) of mobile networks brought about the development of the SIM card. The GSM (Global System for Mobile Communications) standard, adopted by many countries, introduced the concept of a removable SIM card, which could be used in different phones on the same network. This breakthrough allowed users to switch between phones easily without having to re-register with the network.
The early SIM cards were large and bulky, resembling credit cards. Over time, SIM cards have undergone significant size reductions, becoming progressively smaller and more compact. The evolution of SIM card sizes has mirrored the miniaturization of mobile devices, making them easier to incorporate into smartphones and other portable devices.
Types of SIM Cards
The SIM card industry has standardized different sizes of SIM cards to accommodate the shrinking dimensions of mobile devices. The following are the most common types of SIM cards in use today:
- Mini-SIM: This was the standard SIM card size for many years, commonly found in older mobile phones. It measures 25 x 15 millimeters.
- Micro-SIM: Introduced in 2011, the Micro-SIM card is significantly smaller than the Mini-SIM, measuring 15 x 12 millimeters. It became popular with the advent of thinner smartphones.
- Nano-SIM: The smallest SIM card format currently available, measuring 12.3 x 8.8 millimeters. It was introduced in 2012 and is widely used in modern smartphones.
SIM Card Components and Functionality
A SIM card, or Subscriber Identity Module, is a small, removable chip that stores essential information about a mobile phone user. It acts as a bridge between the phone and the mobile network, enabling communication and data transfer.
Key Components of a SIM Card
The SIM card consists of several key components that work together to perform its functions:
- Integrated Circuit (IC): This is the heart of the SIM card, containing the memory and processing power necessary to store and manage user data.
- EEPROM (Electrically Erasable Programmable Read-Only Memory): The EEPROM stores the subscriber’s data, including their phone number, PIN, and other personal information. This data is non-volatile, meaning it persists even when the SIM card is powered off.
- Subscriber Identity Module (SIM): This is the actual physical chip that houses the IC and EEPROM. It is typically embedded in a plastic or metal carrier for protection.
SIM Card Functionality
SIM cards play a crucial role in mobile phone operation, providing the following functions:
- Storing Subscriber Data: The SIM card stores essential information about the user, such as their phone number, PIN, and network settings. This data allows the network to identify and authenticate the user.
- Authentication: When a mobile phone is powered on, the SIM card communicates with the network to authenticate the user. This process ensures that only authorized users can access the network and make calls or use data services.
- Security: SIM cards incorporate security features to protect user data and prevent unauthorized access. The PIN code, for example, adds an extra layer of protection against unauthorized use.
Interaction with the Mobile Network
The interaction between a SIM card and a mobile network is a complex process that involves several steps:
- Power-On: When a mobile phone is powered on, the SIM card sends a signal to the network, identifying itself and requesting a connection.
- Authentication: The network verifies the SIM card’s identity and authenticity using the information stored on the card. This process may involve a PIN check or other security measures.
- Connection Establishment: Once the SIM card is authenticated, the network establishes a connection with the mobile phone, allowing the user to make calls, send messages, and access data services.
- Data Transfer: The SIM card facilitates the transfer of data between the phone and the network. This includes voice calls, SMS messages, and internet data.
SIM Card Security and Privacy
SIM cards play a crucial role in securing mobile communication and protecting user data. They contain sensitive information like personal details, financial data, and access credentials, making their security a paramount concern.
Encryption and Authentication Protocols
SIM cards employ various security mechanisms to safeguard user data and ensure secure communication. These mechanisms include encryption and authentication protocols.
- Encryption: SIM cards use strong encryption algorithms to protect data stored on the card, such as phone numbers, contacts, and messages. This ensures that even if the SIM card is stolen, the data remains inaccessible to unauthorized individuals. For instance, the Advanced Encryption Standard (AES) is a widely used encryption algorithm for SIM cards.
- Authentication Protocols: SIM cards utilize authentication protocols to verify the identity of the user and the device. These protocols involve exchanging cryptographic keys and verifying digital signatures to ensure that only authorized users can access the SIM card and its data. Examples include the 3GPP Authentication and Key Agreement (AKA) protocol and the Secure Element (SE) authentication mechanism.
Potential Vulnerabilities and Threats
Despite the security measures implemented in SIM cards, they are not immune to vulnerabilities and threats. These vulnerabilities can be exploited by malicious actors to gain unauthorized access to user data or compromise the security of the mobile device.
- SIM Cloning: This involves creating a duplicate SIM card with the same information as the original, allowing the attacker to intercept calls, messages, and access user data. This is typically achieved by exploiting vulnerabilities in the SIM card’s operating system or by using specialized cloning devices.
- SIM Card Hacking: Attackers can attempt to hack into the SIM card’s software to gain unauthorized access to the data stored on it. This can involve exploiting vulnerabilities in the SIM card’s firmware or using malware specifically designed to target SIM cards.
- SS7 Attacks: These attacks target the Signaling System 7 (SS7) network, which is responsible for routing calls and messages between mobile devices. By exploiting vulnerabilities in the SS7 network, attackers can intercept communications, track user location, and even redirect calls to their own devices.
Importance of SIM Card Security
SIM card security is crucial for protecting user data and privacy. A compromised SIM card can lead to serious consequences, including:
- Data Theft: Sensitive information stored on the SIM card, such as contact details, financial data, and personal messages, can be stolen and misused by attackers.
- Identity Theft: Attackers can use stolen SIM card data to impersonate the user and access their online accounts or make unauthorized transactions.
- Financial Loss: Access to financial data stored on the SIM card can lead to unauthorized financial transactions, resulting in significant financial losses for the user.
- Privacy Violation: Unauthorized access to the SIM card can compromise the user’s privacy by allowing attackers to monitor their communications, track their location, and access their personal data.
Emerging SIM Technologies
The SIM card technology has undergone significant evolution, leading to the development of newer and more advanced SIM technologies that offer enhanced functionalities and flexibility. These advancements have transformed how users interact with their devices and have opened up new possibilities for mobile communication and data management.
eSIMs
eSIMs, or embedded SIMs, are a revolutionary technology that has the potential to reshape the mobile landscape. They are a digital version of the traditional physical SIM card, offering numerous advantages over their predecessors.
- eSIMs are embedded directly into devices during manufacturing, eliminating the need for physical SIM cards.
- They offer greater flexibility, allowing users to switch between multiple mobile carriers without having to replace the SIM card.
- eSIMs can be provisioned remotely, eliminating the need for physical SIM card swaps.
- eSIMs provide enhanced security features, reducing the risk of SIM card cloning and other security threats.
eSIMs have gained popularity in various applications, including smartphones, tablets, wearables, and IoT devices.
Advantages and Disadvantages of eSIMs
eSIMs present several advantages, including:
- Increased Flexibility: eSIMs enable users to switch between multiple mobile carriers without the need for physical SIM cards. This flexibility is particularly beneficial for travelers who want to use local carriers in different countries or for users who need to access multiple network services.
- Remote Provisioning: eSIMs can be provisioned remotely, eliminating the need for physical SIM card swaps. This simplifies the process of adding new mobile plans or changing carriers, making it more convenient for users.
- Enhanced Security: eSIMs offer enhanced security features, as they are embedded directly into devices and cannot be easily removed or tampered with. This reduces the risk of SIM card cloning and other security threats.
- Space Optimization: eSIMs are significantly smaller than traditional SIM cards, freeing up valuable space within devices for other components.
However, eSIMs also have some disadvantages:
- Limited Compatibility: Not all devices support eSIM technology, and some carriers may not offer eSIM plans.
- Potential for Lock-in: If a carrier restricts the use of eSIMs to their own network, it could limit users’ ability to switch carriers in the future.
- Data Management Challenges: Managing multiple eSIM profiles and data plans can be challenging for some users.
Embedded SIMs
Embedded SIMs (eSIMs) are a type of SIM card that is integrated into a device during manufacturing. They are not removable and offer a more secure and streamlined way to manage mobile connectivity.
Advantages and Disadvantages of Embedded SIMs
Embedded SIMs offer several advantages, including:
- Increased Security: Embedded SIMs are more secure than traditional SIM cards, as they are physically integrated into the device and cannot be easily removed or tampered with.
- Reduced Size and Weight: Embedded SIMs are significantly smaller than traditional SIM cards, freeing up valuable space and reducing the weight of the device.
- Simplified Connectivity Management: Embedded SIMs simplify the process of managing mobile connectivity, as they are pre-configured and do not require physical SIM card swaps.
However, embedded SIMs also have some disadvantages:
- Limited Flexibility: Embedded SIMs are typically locked to a specific carrier or network, limiting users’ ability to switch carriers.
- Device-Specific: Embedded SIMs are device-specific and cannot be transferred to other devices.
- Potential for Lock-in: If a carrier restricts the use of embedded SIMs to their own network, it could limit users’ ability to switch carriers in the future.
Potential Applications and Future Trends of SIM Technology
SIM technology is constantly evolving, with new applications and trends emerging regularly.
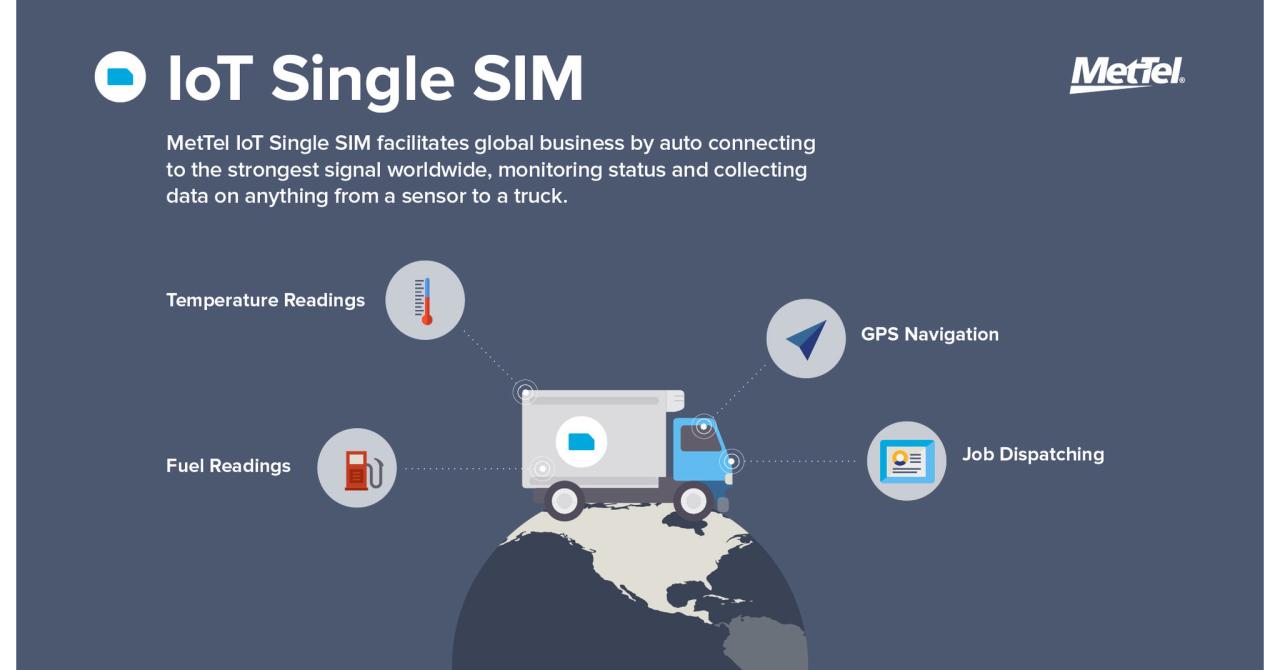
- Internet of Things (IoT): SIM technology is playing a crucial role in the growth of the IoT, enabling connectivity for a wide range of devices, including smart home appliances, wearable devices, and industrial sensors. eSIMs are particularly well-suited for IoT applications, as they offer remote provisioning, enhanced security, and space optimization.
- Mobile Payments: SIM technology is being used to facilitate mobile payments, with SIM-based wallets and contactless payment solutions becoming increasingly popular. eSIMs can enhance the security of mobile payments by providing a secure platform for storing and managing payment information.
- Digital Identity: SIM technology can be used to create secure digital identities, enabling users to authenticate themselves online and access various services. eSIMs can provide a more secure and convenient way to manage digital identities, as they are embedded into devices and cannot be easily tampered with.
- Multi-SIM Functionality: Future SIM technologies may enable devices to support multiple SIM profiles simultaneously, allowing users to access multiple networks and services without having to switch between SIM cards.
- 5G and Beyond: As mobile networks evolve to 5G and beyond, SIM technology will need to adapt to support faster data speeds and increased network capacity. eSIMs and other advanced SIM technologies are expected to play a crucial role in enabling the next generation of mobile communication.
SIM Card Applications and Use Cases

SIM cards have evolved from their initial role in mobile phones to become integral components in a wide range of applications across various industries. Their versatility and ability to store and process data make them valuable assets in diverse use cases.
Mobile Payments
Mobile payments have become increasingly popular, and SIM cards play a crucial role in this technology. SIM-based mobile payments enable users to make secure and convenient transactions using their mobile phones.
- SIM-based mobile payments use the SIM card as a secure element to store sensitive payment information, such as credit card details or digital wallets. This allows users to make purchases without having to carry physical cards or enter their payment details manually.
- Near-Field Communication (NFC) technology is often integrated with SIM cards to enable contactless payments. NFC allows users to make payments by simply tapping their phone against a compatible payment terminal.
- Mobile network operators (MNOs) provide secure payment platforms that leverage the SIM card’s capabilities. These platforms enable users to manage their payment information, track their transactions, and receive notifications about their spending.
Internet of Things (IoT) Devices
The rise of IoT devices has created a demand for secure and reliable connectivity solutions. SIM cards are becoming increasingly essential in connecting IoT devices to the internet.
- Embedded SIM (eSIM) technology enables devices to have multiple SIM profiles stored on a single chip, allowing for flexible connectivity and roaming capabilities. This is particularly beneficial for IoT devices that need to connect to different networks in various locations.
- IoT SIM cards are specifically designed for use in IoT devices. They offer features such as low data rates, long battery life, and secure connectivity, making them ideal for applications like smart meters, wearable devices, and industrial sensors.
- SIM cards can also be used for device authentication and security. They can be used to verify the identity of a device and ensure that it is authorized to access a particular network or service.
Other Emerging Technologies
SIM cards are finding applications in other emerging technologies, such as:
- Digital identity: SIM cards can be used to store and manage digital identities, providing secure and verifiable proof of identity in various applications, including online transactions and access control systems.
- Healthcare: SIM cards can be used to store and transmit patient data securely, enabling remote monitoring and telehealth services.
- Automotive: SIM cards are used in connected cars to provide telematics services, such as navigation, emergency assistance, and remote vehicle diagnostics.
SIM Card Standardization and Regulation
SIM cards, the tiny chips that power our mobile devices, are subject to strict standardization and regulation to ensure interoperability, security, and user privacy. These regulations and standards play a crucial role in shaping the SIM card ecosystem, dictating how SIM cards function, how they interact with mobile networks, and how they are secured.
Role of Standardization Bodies, Sim technology
Standardization bodies play a vital role in defining the specifications and protocols that govern SIM card functionality. These organizations develop and maintain technical standards that ensure interoperability between SIM cards and mobile devices from different manufacturers. This interoperability is essential for users to seamlessly switch between devices and networks without compatibility issues.
- GSM Association (GSMA): The GSMA is a global industry association that represents the interests of mobile operators. It is responsible for developing and maintaining the GSM (Global System for Mobile Communications) standards, which define the core protocols for mobile communication, including SIM card specifications.
- European Telecommunications Standards Institute (ETSI): ETSI is a European standards organization that develops standards for a wide range of telecommunications technologies, including SIM cards. It collaborates with the GSMA and other international organizations to ensure global interoperability.
- International Organization for Standardization (ISO): ISO is a global standards body that develops and publishes international standards for various industries, including telecommunications. ISO standards related to SIM cards address aspects such as security, data formats, and testing procedures.
Regulations and Guidelines
SIM card use and security are subject to regulations and guidelines enforced by national governments and telecommunications authorities. These regulations aim to protect user privacy, prevent fraud, and ensure network security.
- Data Protection Regulations: Data protection laws, such as the General Data Protection Regulation (GDPR) in the European Union, govern the collection, processing, and storage of personal data associated with SIM cards. These regulations ensure that users have control over their personal information and that it is handled responsibly.
- SIM Card Registration: Many countries require SIM card registration to prevent fraud and identify users. Registration typically involves providing personal information, such as name, address, and identity document details, to the mobile operator. This information is then linked to the SIM card.
- SIM Card Security Standards: Regulatory bodies and standardization organizations have established security standards for SIM cards to protect against unauthorized access and data breaches. These standards specify encryption algorithms, authentication protocols, and other security measures that SIM cards must implement.
Impact of Regulatory Changes
Regulatory changes can significantly impact SIM card technology. For example, the introduction of eSIM (embedded SIM) technology has led to new regulations and guidelines addressing its security and interoperability.
- eSIM Regulations: The adoption of eSIMs has prompted regulatory bodies to develop specific guidelines for their use. These guidelines address issues such as eSIM provisioning, security, and consumer protection.
- 5G Security: The rollout of 5G networks has increased the importance of SIM card security. Regulations are evolving to address the security challenges posed by 5G, including the use of advanced encryption and authentication methods.
- Data Privacy: As data privacy concerns continue to grow, regulations are becoming stricter, requiring SIM card manufacturers and mobile operators to implement robust data protection measures. These measures may include data encryption, anonymization, and user consent mechanisms.
SIM Card Management and Administration
Managing SIM cards involves a comprehensive process of provisioning, administration, and security measures to ensure the smooth functioning and security of mobile devices. This section delves into the intricacies of SIM card management, exploring the key aspects, tools, and best practices involved.
SIM Card Provisioning
Provisioning a SIM card involves the initial setup and configuration of the card to enable it to function within a mobile network. This process includes assigning a unique International Mobile Subscriber Identity (IMSI) number, which acts as the SIM card’s identifier. The IMSI is linked to the subscriber’s mobile phone number and other relevant information.
SIM Card Administration
SIM card administration encompasses various tasks related to managing the lifecycle of SIM cards, from provisioning to deactivation. Key administrative tasks include:
- SIM Card Ordering and Allocation: This involves managing the inventory of SIM cards, tracking orders, and allocating cards to subscribers.
- SIM Card Activation and Deactivation: This involves activating new SIM cards for use and deactivating them when they are no longer required. Deactivation can be done for various reasons, such as lost or stolen SIM cards, contract termination, or account suspension.
- SIM Card Profile Management: This involves configuring the SIM card’s profile, which includes settings such as the Mobile Network Operator (MNO) to connect to, data usage limits, and other network-related parameters.
- SIM Card Security Management: This involves implementing security measures to protect SIM cards from unauthorized access and tampering. This includes PIN code management, locking the SIM card, and using secure communication protocols.
- SIM Card Reporting and Analytics: This involves generating reports on SIM card usage, activation and deactivation rates, and other relevant metrics to track performance and identify potential issues.
Tools and Technologies
Several tools and technologies are used for SIM card administration, each with its own set of functionalities and benefits:
- SIM Card Management Systems (SCMS): These are specialized software applications designed to manage the entire SIM card lifecycle, from provisioning to deactivation. SCMS offer centralized control, automated workflows, and comprehensive reporting capabilities. Examples of SCMS include:
- Ericsson’s SIM Card Management System: This system provides comprehensive capabilities for SIM card provisioning, administration, and security management.
- Huawei’s SIM Card Management System: This system offers a range of features for managing SIM cards, including provisioning, activation, deactivation, and security.
- SIM Card Provisioning Servers: These servers are responsible for provisioning and configuring new SIM cards, including assigning IMSI numbers, setting up profiles, and loading applications. They are typically used in conjunction with SCMS.
- SIM Card Security Modules: These hardware modules are used to secure SIM cards and protect them from unauthorized access. They typically implement cryptographic algorithms and secure communication protocols.
- Remote SIM Provisioning (RSP): This technology enables the provisioning and configuration of SIM cards remotely over the air, eliminating the need for physical access to the card. RSP is particularly useful for deploying SIM cards in large-scale deployments or for managing SIM cards in devices that are difficult to access.
Best Practices for Securing and Managing SIM Cards
Ensuring the security and proper management of SIM cards is crucial to protecting sensitive user data and maintaining the integrity of mobile networks. Best practices for securing and managing SIM cards include:
- Use Strong PIN Codes: Choose a strong PIN code for your SIM card and avoid using easily guessed combinations.
- Enable SIM Card Lock: Enable the SIM card lock feature to prevent unauthorized use of your card.
- Regularly Update SIM Card Software: Keep your SIM card software updated to patch vulnerabilities and enhance security.
- Be Cautious of Phishing Attempts: Beware of phishing attempts that try to trick you into revealing your PIN code or other sensitive information.
- Report Lost or Stolen SIM Cards Immediately: If your SIM card is lost or stolen, contact your mobile network operator immediately to report the loss and deactivate the card.
- Use Secure Communication Protocols: Use secure communication protocols such as Transport Layer Security (TLS) or Secure Sockets Layer (SSL) when accessing sensitive information on your SIM card.
- Implement Strong Access Control: Implement strong access control measures to restrict access to SIM card management systems and data to authorized personnel.
- Regularly Audit SIM Card Security: Conduct regular security audits to identify and address potential vulnerabilities in SIM card management systems and processes.
Ultimate Conclusion
As SIM technology continues to evolve, we can expect even more exciting innovations and applications. From the integration of SIM cards in the Internet of Things (IoT) to the emergence of new security protocols, the future of SIM technology holds immense potential. The small but mighty SIM card will continue to play a crucial role in shaping our digital landscape, enabling a world of connected possibilities.
SIM technology has revolutionized the way we connect and communicate. But what about charging our devices on the go? That’s where posicharge technology comes in, offering a seamless and convenient charging experience. With posicharge, you can power up your devices without the need for bulky cables or adapters, allowing you to stay connected even when you’re on the move.