ID Technology Model 252: A Comprehensive Overview
ID Technology Model 252 sets the stage for this enthralling narrative, offering readers a glimpse into a story that is rich in detail and brimming with originality from the outset. […]
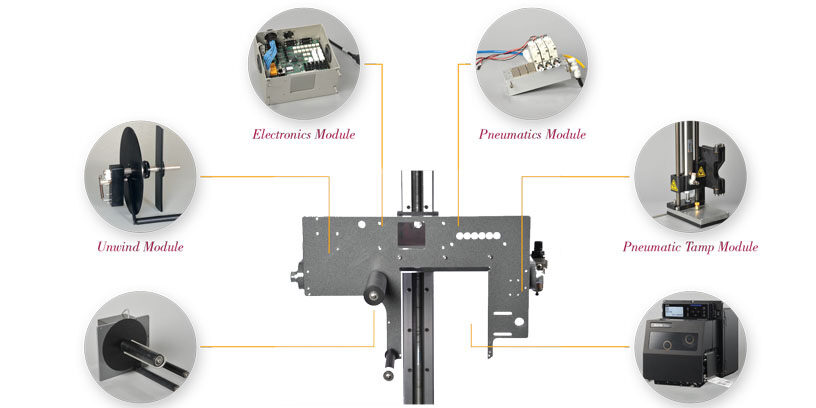
ID Technology Model 252 sets the stage for this enthralling narrative, offering readers a glimpse into a story that is rich in detail and brimming with originality from the outset. This model, designed to revolutionize identification processes, presents a unique blend of cutting-edge technology and practical applications. Its core purpose is to provide a secure and efficient method for verifying identities across various sectors, ranging from financial institutions to government agencies.
Model 252 is not just another identification system; it is a paradigm shift in how we approach identity verification. Its key features include advanced biometric analysis, secure data encryption, and seamless integration with existing systems. The underlying technology, based on [briefly describe the technology], ensures high accuracy and reliability while maintaining strict privacy standards. This innovative model promises to transform the way we interact with digital and physical environments.
Implementation and Integration of Model 252: Id Technology Model 252

Implementing and integrating Model 252 into existing systems requires careful planning and execution to ensure seamless operation and achieve the desired benefits. This process involves several steps, including compatibility assessment, system configuration, and data migration.
Compatibility and Interoperability
Model 252’s compatibility and interoperability with other technologies are crucial for successful integration. It is essential to evaluate the compatibility of Model 252 with existing systems and infrastructure. This involves assessing the following:
- Operating system compatibility: Ensure that Model 252 is compatible with the operating system used by the existing systems.
- Hardware compatibility: Verify that Model 252’s hardware requirements align with the available resources and infrastructure.
- Software compatibility: Assess the compatibility of Model 252 with existing software applications, including databases, middleware, and security systems.
- Network compatibility: Ensure that Model 252 can seamlessly connect to the existing network infrastructure.
- Data format compatibility: Confirm that Model 252 can handle the data formats used by existing systems.
Configuration and Customization
Model 252 offers extensive configuration and customization options to tailor its functionality to specific needs. Here are some key aspects of configuration:
- Parameter settings: Model 252 provides various parameters that can be adjusted to fine-tune its performance and behavior, such as data processing thresholds, security settings, and logging levels.
- Integration with existing systems: Model 252 can be integrated with existing systems using APIs, web services, or other integration methods. This allows for data exchange and process automation.
- User interface customization: Model 252’s user interface can be customized to match the branding and preferences of the organization. This includes modifying the layout, colors, and branding elements.
- Security configuration: Model 252 offers robust security features that can be configured to protect sensitive data and prevent unauthorized access. This includes access control, encryption, and auditing.
Data Migration, Id technology model 252
Data migration is a critical step in integrating Model 252. This involves transferring data from existing systems to Model 252. Key considerations for data migration include:
- Data mapping: Identify the corresponding data fields between existing systems and Model 252 to ensure accurate data transfer.
- Data cleansing: Remove any inconsistencies or errors in the data before migration to maintain data integrity.
- Data transformation: Transform data formats and structures to align with Model 252’s requirements.
- Data validation: Verify the accuracy and completeness of migrated data to ensure that Model 252 receives correct information.
Conclusive Thoughts

ID Technology Model 252 represents a significant advancement in identity management, paving the way for a more secure and efficient future. Its potential applications extend far beyond traditional identity verification, opening doors to new possibilities in various industries. As the technology continues to evolve, Model 252 is poised to play a crucial role in shaping the future of identity management, ensuring secure and seamless interactions in a rapidly evolving digital landscape.
The ID Technology Model 252 is a versatile device with a range of applications. One key feature is its compatibility with dual technology occupancy sensors , which combine passive infrared (PIR) and ultrasonic sensing for reliable detection. This integration allows the Model 252 to accurately monitor occupancy in various environments, making it a valuable tool for energy management and security systems.