Endpoint Application Isolation & Containment: Securing Modern Endpoints
Endpoint application isolation and containment technology represents a paradigm shift in endpoint security. It focuses on creating a secure environment where applications are isolated from each other and the underlying […]
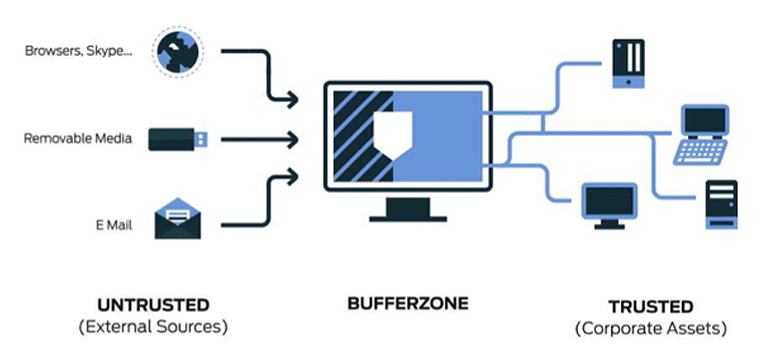
Endpoint application isolation and containment technology represents a paradigm shift in endpoint security. It focuses on creating a secure environment where applications are isolated from each other and the underlying operating system, significantly reducing the attack surface and minimizing the impact of potential threats. This technology is crucial in today’s dynamic threat landscape, where malware, ransomware, and zero-day exploits are constantly evolving.
Imagine a scenario where an employee clicks on a malicious link in an email. Without isolation, the malware could easily spread across the entire system, potentially compromising sensitive data. However, with endpoint application isolation and containment, the malware is confined to a sandboxed environment, preventing it from accessing critical system resources and causing widespread damage.
Endpoint Application Isolation and Containment
Endpoint application isolation and containment technology is a security approach that aims to limit the impact of malicious software by separating applications and their data from the underlying operating system and other applications. This technology essentially creates a secure “sandbox” environment where applications can run without directly accessing the host system’s resources, effectively preventing malware from spreading and causing damage.
Benefits of Endpoint Application Isolation and Containment
Endpoint application isolation and containment technology offers several key benefits:
- Reduced Attack Surface: By isolating applications, the attack surface is significantly reduced, making it more difficult for malware to exploit vulnerabilities and gain access to sensitive data.
- Enhanced Security Posture: This technology strengthens the overall security posture of endpoints by creating a more robust defense against malware and other threats.
- Improved Data Protection: Isolation and containment prevent malicious applications from accessing and manipulating critical data, ensuring data integrity and confidentiality.
- Simplified Security Management: This technology simplifies security management by reducing the complexity of patching and updating applications.
Real-World Scenarios
Endpoint application isolation and containment technology is crucial in various real-world scenarios:
- Healthcare: In healthcare, where patient data is highly sensitive, this technology helps protect against ransomware attacks that could compromise medical records and disrupt critical operations.
- Financial Institutions: Financial institutions rely heavily on endpoint application isolation to safeguard sensitive financial data from cyberattacks, preventing unauthorized access and financial losses.
- Government Agencies: Government agencies handle classified information and critical infrastructure, making endpoint application isolation essential for protecting sensitive data and ensuring national security.
Key Features and Mechanisms
Endpoint application isolation and containment technologies are designed to protect endpoints from threats by limiting the attack surface and preventing malicious software from spreading. They achieve this by creating a secure environment for applications to run in, effectively isolating them from the underlying operating system and other applications. This isolation helps to contain the impact of any successful attack, limiting the damage that can be inflicted on the endpoint and the network.
Isolation Techniques
Different isolation techniques are employed to create a secure environment for applications to run in. These techniques are often used in combination to provide comprehensive protection.
- Sandboxing: Sandboxing is a popular isolation technique that creates a controlled environment where applications can run without affecting the host system. This environment is isolated from the operating system and other applications, preventing malicious software from accessing critical system resources or spreading to other parts of the system. Sandboxes typically restrict the application’s access to the system’s resources and network, preventing it from making changes to the host system or communicating with external systems without permission. This isolation helps to prevent the spread of malware and protect sensitive data.
- Virtualization: Virtualization creates a virtual environment where applications run in isolated virtual machines (VMs). These VMs are completely separate from the host system and other VMs, offering a high level of isolation. This isolation ensures that any malicious activity within a VM cannot affect the host system or other VMs. Virtualization allows for greater flexibility and scalability, enabling organizations to run multiple applications in isolation on a single physical machine.
- Microsegmentation: Microsegmentation is a network security technique that isolates applications and systems within a network. It involves dividing the network into smaller segments, with each segment containing a specific group of applications or systems. This approach restricts communication between segments, preventing malicious software from spreading across the network. By isolating applications and systems, microsegmentation helps to limit the impact of a security breach, preventing attackers from gaining access to other parts of the network.
Containment Mechanisms
Endpoint application isolation and containment technologies use a variety of containment mechanisms to prevent malicious software from spreading and causing harm. These mechanisms work in conjunction with isolation techniques to create a robust security posture.
- Network Segmentation: Network segmentation is a key containment mechanism that divides the network into smaller segments, limiting the communication between different segments. This helps to prevent the spread of malware by restricting its movement within the network. By isolating critical systems and applications, network segmentation reduces the attack surface and makes it more difficult for attackers to gain access to sensitive data.
- Application Whitelisting: Application whitelisting is a security policy that only allows known and trusted applications to run on the endpoint. This policy restricts the execution of any application that is not explicitly whitelisted, preventing the execution of malicious software. Application whitelisting is an effective way to prevent the execution of unknown or untrusted applications, significantly reducing the risk of malware infections.
- Behavior Analysis: Behavior analysis is a technique that monitors the behavior of applications and systems for any suspicious activity. This analysis can identify potential threats by detecting unusual patterns or behaviors that indicate malicious activity. Behavior analysis can detect zero-day threats that are not yet known to antivirus software, providing an additional layer of protection.
Implementation and Deployment
Implementing endpoint application isolation and containment technology involves a systematic approach that ensures effective integration with existing infrastructure and user workflows. This section delves into the key steps involved in deployment, explores different deployment models, and provides best practices for configuration and management.
Deployment Models
Deployment models determine how endpoint application isolation and containment technology is integrated into an organization’s IT environment. Each model presents unique advantages and disadvantages, influencing factors like cost, complexity, and scalability.
- Agent-Based: This model utilizes software agents installed on individual endpoints. Agents enforce isolation policies and monitor application behavior. This approach offers granular control over specific devices and applications. However, it requires installation and management on each endpoint, potentially increasing administrative overhead.
- Host-Based: This model relies on software installed on the host operating system, typically a hypervisor or virtual machine manager. Host-based solutions provide centralized management and control over multiple endpoints. However, they might not offer the same level of granular control as agent-based solutions.
- Cloud-Based: This model leverages cloud services to deliver and manage endpoint application isolation and containment capabilities. Cloud-based solutions offer scalability, flexibility, and reduced infrastructure management responsibilities. However, they may introduce dependencies on cloud providers and potential security concerns regarding data storage and access.
Configuration and Management Best Practices
Proper configuration and ongoing management are crucial for optimizing the effectiveness of endpoint application isolation and containment technology. These best practices help ensure secure and efficient operations:
- Define Clear Isolation Policies: Establish comprehensive isolation policies that specify which applications are allowed or restricted on endpoints. Consider factors like application type, user roles, and sensitivity of data accessed.
- Regularly Update Policies and Configurations: As new applications emerge and threats evolve, it’s essential to update isolation policies and configurations to maintain effectiveness.
- Monitor Application Behavior: Continuously monitor application behavior to identify potential threats and anomalies. This helps detect unauthorized or malicious activity.
- Implement Strong Authentication and Access Control: Ensure robust authentication mechanisms and granular access control measures to prevent unauthorized access to isolated applications.
- Regularly Patch and Update Software: Keep endpoint software, including operating systems, applications, and isolation tools, up-to-date with the latest security patches to address vulnerabilities.
- Implement Security Awareness Training: Train users on best practices for secure application usage, including identifying suspicious activities and reporting potential security threats.
Security Benefits and Risk Mitigation: Endpoint Application Isolation And Containment Technology
Endpoint application isolation and containment technology significantly enhances endpoint security by creating a protected environment for applications and data. This technology effectively mitigates various cyber threats, including malware, ransomware, and zero-day exploits, by isolating applications from the underlying operating system and network.
Effectiveness in Mitigating Cyber Threats, Endpoint application isolation and containment technology
This technology effectively mitigates cyber threats by creating a secure environment where applications are isolated from the underlying operating system and network. This isolation prevents malicious code from spreading to other applications or the host system.
- Malware: Endpoint application isolation and containment technology effectively prevents malware from spreading to other applications or the host system. This isolation prevents malicious code from accessing sensitive data or system resources. For example, if a user downloads a malicious file, the isolated application environment will prevent the malware from accessing the user’s files or system resources.
- Ransomware: By isolating applications from the host system, this technology can prevent ransomware from encrypting critical files and data. This isolation prevents ransomware from accessing sensitive data or system resources. For example, if a user opens a ransomware-infected email attachment, the isolated application environment will prevent the ransomware from encrypting the user’s files or system resources.
- Zero-day Exploits: This technology helps mitigate the impact of zero-day exploits by isolating applications from the underlying operating system. This isolation prevents attackers from exploiting vulnerabilities in the operating system or other applications. For example, if an attacker exploits a vulnerability in the operating system, the isolated application environment will prevent the attacker from accessing the user’s files or system resources.
Comparison with Traditional Endpoint Security Solutions
Endpoint application isolation and containment technology offers significant advantages over traditional endpoint security solutions.
- Traditional endpoint security solutions rely on signature-based detection and prevention mechanisms. These solutions are often ineffective against new and unknown threats, such as zero-day exploits.
- Endpoint application isolation and containment technology, on the other hand, provides a more proactive approach to security by isolating applications from the underlying operating system and network. This approach effectively mitigates the impact of both known and unknown threats.
- Traditional endpoint security solutions often have a significant performance impact on the host system.
- Endpoint application isolation and containment technology, however, has minimal performance impact on the host system as it operates in a separate environment.
Performance and Usability Considerations
Endpoint application isolation and containment technologies can have a significant impact on system performance and user experience. Understanding these potential trade-offs is crucial for effective implementation and adoption.
Performance Impact
The overhead introduced by these technologies can affect system performance.
- Resource Consumption: Isolation and containment mechanisms require additional resources, such as memory and CPU cycles, to monitor and enforce application behavior. This can lead to increased resource utilization and potentially impact overall system performance, especially on resource-constrained devices.
- Network Latency: Communication between isolated applications and the underlying operating system or other applications may experience increased latency due to the added layers of security enforcement. This can affect the responsiveness of applications and the overall user experience.
- Application Compatibility: Some applications may not be compatible with the isolation and containment mechanisms employed. This can result in application failures or unexpected behavior, leading to performance issues and usability challenges.
Usability Considerations
The user experience and administrative overhead associated with endpoint application isolation and containment technologies are important factors to consider.
- User Experience: Users may encounter limitations in their ability to interact with isolated applications, such as restricted access to certain functionalities or the inability to share data between isolated applications. This can impact user productivity and satisfaction.
- Administrative Overhead: Implementing and managing these technologies can require significant administrative effort, including configuring policies, managing exceptions, and troubleshooting issues. This overhead can be substantial, especially in large organizations with many endpoints.
Performance Optimization and Usability Enhancement
To mitigate the potential performance impact and enhance usability, several strategies can be employed.
- Optimize Configuration: Fine-tuning the isolation and containment policies to balance security and performance is crucial. This may involve defining granular policies based on application types, user roles, and network contexts. Regularly reviewing and adjusting these policies based on performance monitoring data is essential.
- Hardware Resources: Ensuring sufficient hardware resources, such as memory and CPU, is critical for optimal performance. Consider upgrading hardware or optimizing resource allocation to accommodate the increased resource demands of these technologies.
- Application Compatibility: Thoroughly test applications for compatibility with the chosen isolation and containment technology. Identify and address any compatibility issues proactively to prevent performance problems and usability challenges.
- User Training: Provide users with comprehensive training on the new security measures and how to interact with isolated applications. This can help minimize user frustration and improve overall productivity.
- Centralized Management: Implement centralized management tools to streamline the configuration, monitoring, and troubleshooting of endpoint application isolation and containment technologies. This can reduce administrative overhead and improve overall efficiency.
Industry Standards and Compliance
Endpoint application isolation and containment technologies play a crucial role in enhancing security posture and ensuring compliance with industry standards and regulations. These technologies are designed to limit the impact of malicious software and prevent unauthorized access to sensitive data, aligning with security best practices and regulatory requirements.
Alignment with Security Best Practices
Endpoint application isolation and containment technologies are closely aligned with several security best practices, including:
- Principle of Least Privilege: By isolating applications within secure containers, these technologies enforce the principle of least privilege, granting applications only the necessary permissions to function. This minimizes the attack surface and reduces the potential impact of a successful compromise.
- Defense in Depth: These technologies contribute to a layered security approach by creating an additional barrier between applications and the underlying operating system. This layered approach provides multiple levels of protection against threats.
- Data Protection: Endpoint application isolation technologies help protect sensitive data by preventing unauthorized access and modification. By isolating applications within secure containers, these technologies ensure that even if one application is compromised, the data remains protected.
Compliance with Regulations
Endpoint application isolation and containment technologies can help organizations achieve compliance with various regulations, including:
- Payment Card Industry Data Security Standard (PCI DSS): These technologies can help organizations meet PCI DSS requirements by isolating payment processing applications and preventing unauthorized access to sensitive cardholder data.
- Health Insurance Portability and Accountability Act (HIPAA): These technologies can help organizations meet HIPAA requirements by isolating healthcare applications and protecting patient health information (PHI).
- General Data Protection Regulation (GDPR): These technologies can help organizations meet GDPR requirements by isolating applications that process personal data and ensuring that only authorized personnel have access to this data.
Examples of Compliance Achievement
- Financial Institutions: Banks and other financial institutions can use endpoint application isolation technologies to isolate online banking applications and prevent unauthorized access to customer accounts. This helps them comply with PCI DSS requirements and maintain customer trust.
- Healthcare Providers: Hospitals and clinics can use endpoint application isolation technologies to isolate electronic health record (EHR) systems and prevent unauthorized access to patient data. This helps them comply with HIPAA regulations and protect patient privacy.
- Government Agencies: Government agencies can use endpoint application isolation technologies to isolate sensitive applications and prevent unauthorized access to classified information. This helps them comply with government security regulations and protect national security.
Future Trends and Developments
Endpoint application isolation and containment technology is constantly evolving to address the ever-changing landscape of cyber threats. Emerging trends are driven by advancements in technology, evolving attack vectors, and the growing need for robust security solutions.
Impact of Artificial Intelligence and Machine Learning
Artificial intelligence (AI) and machine learning (ML) are playing an increasingly significant role in endpoint security. These technologies can enhance the effectiveness of endpoint application isolation and containment in several ways:
- Automated Threat Detection and Response: AI and ML algorithms can analyze vast amounts of data from various sources, including network traffic, endpoint behavior, and threat intelligence feeds, to identify suspicious activities and potential threats in real-time. This enables automated threat detection and response, reducing the time it takes to identify and neutralize threats.
- Adaptive Security Policies: AI and ML can learn from past attacks and adapt security policies dynamically to better protect endpoints. This includes identifying and isolating applications based on their risk profiles and adjusting security settings based on real-time threat intelligence.
- Enhanced Anomaly Detection: AI and ML algorithms can identify deviations from normal endpoint behavior, which can indicate malicious activity. This helps to detect zero-day attacks and other novel threats that traditional security solutions may miss.
“By 2025, 75% of organizations will use AI-powered security solutions to improve their threat detection and response capabilities.” – Gartner
Future Direction of Endpoint Security
As cyber threats continue to evolve, the future of endpoint security is likely to focus on:
- Zero Trust Security: This approach assumes that no user or device can be trusted by default, requiring strict verification and authentication before access is granted. Endpoint application isolation and containment play a crucial role in implementing a Zero Trust model by limiting the impact of compromised endpoints.
- Threat Hunting and Proactive Security: Traditional reactive security measures are becoming less effective as attackers use increasingly sophisticated techniques. Proactive security measures, such as threat hunting and automated incident response, will become increasingly important. AI and ML can be used to automate these processes, making it easier to identify and neutralize threats before they cause significant damage.
- Integration with Cloud Security Solutions: The increasing adoption of cloud computing has led to a growing need for integrated security solutions that span on-premises and cloud environments. Endpoint application isolation and containment technologies will need to integrate seamlessly with cloud security platforms to provide comprehensive protection.
Conclusive Thoughts

Endpoint application isolation and containment technology is a powerful tool for enhancing endpoint security, mitigating cyber threats, and ensuring business continuity. By implementing this technology, organizations can create a more secure and resilient IT environment, safeguarding their data and operations from malicious actors. As cyber threats continue to evolve, endpoint application isolation and containment will play an increasingly vital role in protecting critical systems and data.
Endpoint application isolation and containment technology is crucial for protecting sensitive data and preventing malware from spreading. Imagine a scenario where a user accidentally downloads a malicious file. With strong isolation measures in place, the threat would be contained to that specific application, preventing it from affecting the entire system.
Similarly, the innovative GE steam technology dryer utilizes a closed system to prevent water from escaping, ensuring efficient and safe operation. Just like the dryer’s contained environment protects its components, endpoint isolation technology safeguards your digital assets from external threats.