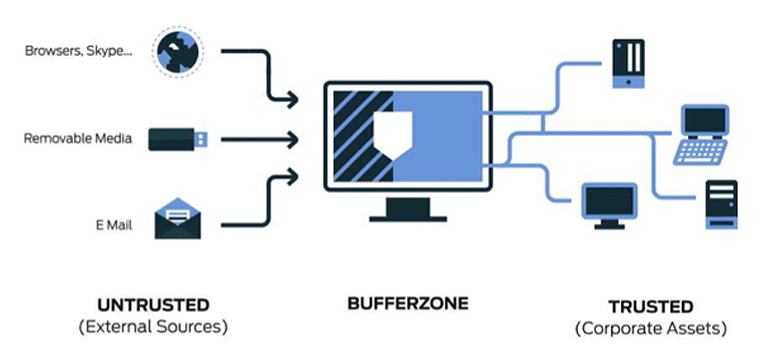
Emerging Technologies in Cybersecurity C844: A Look at the Future
Emerging technologies in cybersecurity C844 sets the stage for a fascinating exploration of how innovation is shaping the future of digital security. The digital landscape is constantly evolving, with new […]
Emerging technologies in cybersecurity C844 sets the stage for a fascinating exploration of how innovation is shaping the future of digital security. The digital landscape is constantly evolving, with new threats emerging at an alarming rate. To stay ahead of these threats, cybersecurity professionals must embrace cutting-edge technologies that can enhance protection and resilience.
This comprehensive guide delves into the transformative potential of artificial intelligence (AI), blockchain technology, quantum computing, biometric authentication, and Internet of Things (IoT) security. We’ll examine how these technologies are being harnessed to bolster defenses, mitigate risks, and pave the way for a more secure digital world. Additionally, we’ll explore the ethical considerations that arise from the implementation of these emerging technologies, ensuring that security advancements are balanced with responsible practices.
Introduction
Cybersecurity is the practice of protecting computer systems and networks from unauthorized access, use, disclosure, disruption, modification, or destruction. Emerging technologies are new technologies that are still under development or have recently been introduced to the market.
The cybersecurity landscape is constantly evolving as cybercriminals become more sophisticated in their attacks. Emerging technologies can help organizations stay ahead of these threats by providing new ways to detect, prevent, and respond to attacks.
The Evolving Landscape of Cyber Threats, Emerging technologies in cybersecurity c844
The evolution of cyber threats is driven by various factors, including:
- Increasing sophistication of attackers: Cybercriminals are constantly developing new techniques and tools to bypass security measures. They are also collaborating with each other to share information and resources, making them more effective.
- Growth of the Internet of Things (IoT): The increasing number of connected devices creates new attack surfaces for cybercriminals. These devices often have weak security measures, making them vulnerable to attacks.
- Rise of cloud computing: Cloud computing has made it easier for organizations to access and share data, but it has also created new security challenges. Organizations need to ensure that their cloud environments are secure and that they have adequate controls in place to protect their data.
These threats necessitate the development of innovative cybersecurity solutions to counter them effectively. Emerging technologies play a crucial role in this regard.
Artificial Intelligence (AI) in Cybersecurity
Artificial intelligence (AI) is revolutionizing the cybersecurity landscape, offering powerful tools to combat evolving threats. By leveraging the capabilities of AI, organizations can enhance their defenses, improve threat detection, and automate security tasks.
AI in Threat Detection and Analysis
AI plays a crucial role in identifying and analyzing potential threats. AI algorithms can analyze vast amounts of data from various sources, such as network traffic, security logs, and user behavior, to detect patterns and anomalies that might indicate malicious activity.
- Machine Learning (ML): ML algorithms are trained on historical data to learn patterns and identify deviations from normal behavior. These algorithms can be used to detect suspicious activities, such as unusual login attempts, network traffic patterns, and file access patterns.
- Deep Learning (DL): DL is a subset of ML that uses artificial neural networks to learn complex relationships in data. DL algorithms can be used to analyze large datasets of network traffic, identify malware signatures, and detect phishing attacks.
- Natural Language Processing (NLP): NLP techniques are used to analyze textual data, such as emails, social media posts, and security alerts. NLP can help identify phishing emails, detect malware distribution campaigns, and monitor online threats.
Examples of AI-Powered Security Tools
Several AI-powered security tools are available to organizations, including:
- Intrusion Detection Systems (IDS): AI-powered IDS can analyze network traffic and identify suspicious patterns, such as known attack signatures and anomalous behavior. These systems can automatically block malicious traffic and alert security teams to potential threats.
- Malware Analysis Platforms: AI-powered malware analysis platforms use ML and DL algorithms to automatically analyze suspicious files and identify malicious code. These platforms can detect new and unknown malware variants, reducing the time it takes to respond to threats.
- Security Information and Event Management (SIEM): AI-powered SIEM systems can analyze security logs from various sources, identify potential threats, and generate alerts. AI can help SIEM systems prioritize alerts, reduce noise, and improve the efficiency of security teams.
AI Techniques Used in Cybersecurity
| AI Technique | Description | Cybersecurity Applications |
|---|---|---|
| Machine Learning | Algorithms trained on historical data to identify patterns and anomalies. | Intrusion detection, malware analysis, phishing detection. |
| Deep Learning | Uses artificial neural networks to learn complex relationships in data. | Network traffic analysis, malware classification, threat intelligence. |
| Natural Language Processing | Analyzes textual data, such as emails and social media posts. | Phishing detection, malware distribution analysis, threat intelligence. |
Blockchain Technology for Cybersecurity
Blockchain technology has emerged as a promising solution to enhance cybersecurity by offering a decentralized and immutable ledger that can track and verify data transactions. This technology can significantly strengthen data security and integrity, making it an attractive option for various cybersecurity applications.
Blockchain for Secure Authentication and Access Control
Blockchain can be used to implement secure authentication and access control mechanisms. By leveraging cryptographic techniques, blockchain enables the creation of digital identities that are unique, verifiable, and tamper-proof. This eliminates the need for centralized authentication systems, which are vulnerable to attacks.
- Each user’s identity is stored on the blockchain, creating a decentralized identity management system.
- Transactions involving user authentication and access control are recorded on the blockchain, providing a transparent and auditable trail.
- The decentralized nature of blockchain makes it difficult for malicious actors to compromise the system or forge identities.
Blockchain for Data Provenance Tracking
Blockchain can be used to track the origin and history of data, ensuring its authenticity and integrity. Every modification or transaction involving data is recorded on the blockchain, creating an immutable audit trail.
- Blockchain technology allows for the creation of a tamper-proof record of data transactions, making it possible to trace data back to its source.
- This capability is particularly valuable in situations where data integrity is critical, such as in supply chain management or healthcare records.
- By tracking data provenance, organizations can detect and prevent data manipulation or fraudulent activities.
Blockchain-Based Cybersecurity Solutions
Several blockchain-based cybersecurity solutions are emerging, addressing various security challenges.
- Distributed Ledgers: Blockchain-based distributed ledgers provide a secure and transparent platform for storing and sharing sensitive data. By distributing data across multiple nodes, distributed ledgers make it more difficult for attackers to compromise the entire system.
- Secure Identity Management Systems: Blockchain-based identity management systems offer a decentralized and secure way to manage user identities and access control. These systems eliminate the need for centralized authorities and provide greater control over personal data.
- Secure Data Sharing Platforms: Blockchain technology can facilitate secure data sharing between different organizations, ensuring data integrity and privacy. By using blockchain, organizations can share data without compromising their security or privacy.
Comparison of Traditional Cybersecurity Methods with Blockchain-Based Approaches
| Feature | Traditional Cybersecurity Methods | Blockchain-Based Approaches |
|---|---|---|
| Data Security | Relies on centralized systems and encryption techniques. | Offers decentralized and immutable data storage, enhancing security and integrity. |
| Authentication | Uses centralized authentication servers that can be vulnerable to attacks. | Provides decentralized and tamper-proof authentication mechanisms using cryptographic techniques. |
| Data Provenance | Difficult to track data origin and history. | Enables immutable tracking of data transactions, ensuring data authenticity and integrity. |
| Transparency | Limited transparency in data transactions. | Provides a transparent and auditable trail of data transactions, increasing accountability. |
| Scalability | Can be challenging to scale traditional security systems. | Offers potential for scalability and flexibility due to its decentralized nature. |
Quantum Computing and Cybersecurity: Emerging Technologies In Cybersecurity C844

Quantum computing is a rapidly evolving field with the potential to revolutionize cybersecurity. It harnesses the principles of quantum mechanics to perform computations in ways that are impossible for classical computers. This technology presents both opportunities and challenges for cybersecurity professionals.
Impact on Encryption Algorithms
Quantum computers pose a significant threat to the encryption algorithms that underpin modern cybersecurity. Traditional encryption methods rely on the difficulty of factoring large numbers, a problem that is computationally intractable for classical computers. However, quantum computers can factor these numbers efficiently using algorithms like Shor’s algorithm. This means that quantum computers could break widely used encryption algorithms such as RSA and ECC, potentially compromising the confidentiality and integrity of sensitive data.
Quantum-Resistant Cryptography
In response to the threat posed by quantum computers, researchers are developing quantum-resistant cryptography (QRC). QRC algorithms are designed to be secure against attacks by both classical and quantum computers. These algorithms rely on different mathematical problems that are believed to be difficult for both types of computers to solve. Examples of QRC algorithms include lattice-based cryptography, code-based cryptography, and multivariate cryptography.
Cybersecurity Applications of Quantum Computing
While quantum computers pose a threat to existing encryption algorithms, they also offer exciting opportunities for enhancing cybersecurity. Quantum computers can be used to develop new and more powerful security tools.
- Advanced Threat Detection: Quantum computers can analyze vast amounts of data and identify patterns that are difficult or impossible for classical computers to detect. This can be used to develop more effective intrusion detection systems (IDS) and malware detection tools. For example, quantum computers could be used to analyze network traffic in real-time, identifying anomalies that could indicate malicious activity.
- Vulnerability Analysis: Quantum computers can be used to perform more efficient and accurate vulnerability analysis. This can help organizations identify and patch vulnerabilities in their systems before they can be exploited by attackers. For instance, quantum computers could be used to simulate the behavior of complex systems, revealing weaknesses that might otherwise be missed.
- Quantum Key Distribution (QKD): QKD is a secure communication method that uses quantum mechanics to generate and distribute encryption keys. QKD is highly resistant to eavesdropping and can provide a more secure alternative to traditional key exchange protocols. QKD is a promising technology for securing critical infrastructure and sensitive communications.
Challenges and Opportunities
The integration of quantum computing into cybersecurity presents both challenges and opportunities.
- Scalability and Cost: Quantum computers are still in their early stages of development and are currently very expensive to build and operate. Scaling quantum computers to a level where they can be widely used in cybersecurity applications is a significant challenge. Furthermore, the cost of developing and deploying quantum-resistant cryptography can be prohibitive for some organizations.
- Standardization and Implementation: The development of quantum-resistant cryptography is still ongoing, and there is no single standardized approach. This lack of standardization can make it difficult for organizations to implement QRC effectively. Furthermore, implementing QRC requires significant changes to existing infrastructure and processes.
- Research and Development: Significant investment in research and development is needed to advance quantum computing and QRC. Governments, universities, and private companies need to collaborate to ensure that these technologies are developed responsibly and effectively.
Biometric Authentication and Cybersecurity
Biometric authentication has emerged as a robust alternative to traditional password-based methods, offering enhanced security and user convenience. It leverages unique biological characteristics to verify identity, making it more difficult for unauthorized individuals to gain access.
Principles and Advantages of Biometric Authentication
Biometric authentication relies on the principle of verifying an individual’s identity by comparing their unique biological traits against a stored template. These traits, such as fingerprints, facial features, or iris patterns, are distinct and difficult to replicate. Unlike passwords, which can be easily forgotten or stolen, biometric data is inherently linked to the individual and cannot be easily compromised.
- Enhanced Security: Biometric authentication offers a significant security advantage over traditional password-based methods. Biometric data is difficult to forge or steal, making it a more reliable form of authentication.
- Increased Convenience: Biometric authentication eliminates the need for users to remember complex passwords or carry physical tokens. It streamlines the authentication process, making it more convenient for users.
- Improved User Experience: Biometric authentication provides a seamless and intuitive user experience. Users can access systems and services quickly and easily without having to remember passwords or enter PINs.
Biometric Technologies
Various biometric technologies are employed in cybersecurity, each with its own strengths and weaknesses.
- Facial Recognition: Facial recognition technology analyzes unique facial features to identify individuals. It involves capturing a live image of a person’s face and comparing it to a stored template. This technology is widely used in access control systems, identity verification, and surveillance applications.
- Fingerprint Scanning: Fingerprint scanning involves capturing and analyzing the unique pattern of ridges and valleys on a person’s fingertips. It is a highly reliable and widely adopted biometric technology used in smartphones, laptops, and access control systems.
- Iris Scanning: Iris scanning utilizes the unique patterns and structures within the iris of a person’s eye for identification. This technology is considered highly accurate and secure, making it suitable for high-security applications.
- Voice Recognition: Voice recognition technology analyzes the unique characteristics of a person’s voice, such as pitch, tone, and rhythm, to authenticate their identity. It is commonly used in voice assistants, mobile banking applications, and access control systems.
Biometric Authentication Systems in Cybersecurity
Biometric authentication systems are employed in various cybersecurity applications, including:
- Access Control: Biometric authentication systems are used to control access to physical and digital resources, such as buildings, computers, and sensitive data. They ensure that only authorized individuals can access these resources.
- Identity Verification: Biometric authentication is used to verify the identity of individuals during online transactions, account registration, and other online activities. This helps prevent identity theft and fraud.
- Two-Factor Authentication: Biometric authentication can be combined with other authentication factors, such as passwords or PINs, to create a more secure two-factor authentication system.
Security Implications of Biometric Technologies
While biometric authentication offers significant advantages, it also presents unique security challenges:
- Privacy Concerns: Biometric data is sensitive and should be handled with care. Unauthorized access or misuse of this data can lead to privacy violations.
- Spoofing and False Acceptance: Biometric systems can be susceptible to spoofing attacks, where attackers use fake biometric data to gain unauthorized access.
- Data Security: Biometric data must be securely stored and protected from unauthorized access. Data breaches can compromise the security of biometric systems.
- Accuracy and Reliability: Biometric systems should be accurate and reliable to avoid false acceptance or rejection rates. High error rates can lead to security vulnerabilities and user frustration.
Ethical Considerations in Cybersecurity

The rapid advancement of emerging technologies in cybersecurity presents a complex ethical landscape. While these technologies offer significant benefits in protecting our digital lives, they also raise concerns about data privacy, surveillance, and potential bias in algorithms. It is crucial to consider these ethical implications and ensure the responsible development and deployment of these technologies.
Data Privacy and Surveillance
Data privacy is a fundamental human right that is increasingly threatened by the proliferation of data collection and analysis tools. Cybersecurity technologies, such as AI-powered intrusion detection systems and behavioral analytics, rely heavily on the collection and analysis of personal data. This raises concerns about the potential for misuse of this data for surveillance purposes.
- For example, facial recognition technology, while effective in identifying individuals, can be used for mass surveillance, potentially infringing on individual privacy and freedom.
- Similarly, the use of AI-powered systems to monitor employee activity can raise concerns about workplace privacy and the potential for unfair or discriminatory practices.
It is essential to establish clear legal frameworks and ethical guidelines that protect individuals’ privacy while enabling the effective use of cybersecurity technologies.
Bias in AI Algorithms
AI algorithms are trained on massive datasets, and if these datasets contain biases, these biases can be reflected in the algorithms’ outputs. This can lead to discriminatory outcomes in cybersecurity applications.
- For example, an AI-powered fraud detection system trained on a dataset that disproportionately represents certain demographics may be more likely to flag transactions by individuals from those demographics as fraudulent.
- Similarly, an AI-powered hiring system trained on biased data may favor candidates from certain backgrounds, perpetuating existing inequalities.
It is crucial to develop and implement mechanisms to identify and mitigate bias in AI algorithms used in cybersecurity. This includes careful selection of training data, regular audits of algorithms, and transparency in decision-making processes.
Role of Cybersecurity Professionals
Cybersecurity professionals play a critical role in promoting ethical and responsible use of emerging technologies. They must be aware of the ethical implications of their work and strive to develop and deploy technologies that respect human rights and promote social good.
- They should advocate for policies that protect data privacy and prevent the misuse of surveillance technologies.
- They should also be proactive in identifying and mitigating bias in AI algorithms, ensuring that these technologies are used fairly and equitably.
Cybersecurity professionals must also engage in ongoing dialogue with stakeholders, including policymakers, researchers, and the public, to ensure that emerging technologies are developed and deployed in an ethical and responsible manner.
Ethical Frameworks and Guidelines
Several ethical frameworks and guidelines have been developed to address the ethical considerations in cybersecurity.
- The IEEE Global Initiative on Ethics of Autonomous and Intelligent Systems provides a framework for ethical considerations in the development and deployment of AI systems.
- The European Union’s General Data Protection Regulation (GDPR) establishes comprehensive data privacy regulations that aim to protect individuals’ personal data.
These frameworks and guidelines provide valuable guidance for cybersecurity professionals in navigating the ethical complexities of emerging technologies.
Potential Risks and Benefits
Emerging technologies in cybersecurity offer significant potential benefits, such as improved threat detection, enhanced security posture, and more efficient incident response. However, these technologies also pose potential risks, including the erosion of privacy, the potential for misuse, and the perpetuation of existing biases.
- For example, the use of AI-powered intrusion detection systems can significantly improve threat detection capabilities, but it also raises concerns about the potential for false positives and the misuse of data for surveillance purposes.
- Similarly, the use of blockchain technology for secure data storage can enhance data integrity and security, but it also raises concerns about the potential for data breaches and the lack of transparency in blockchain transactions.
It is essential to carefully consider the potential risks and benefits of emerging technologies and to develop and implement appropriate safeguards to mitigate potential risks.
Final Review
As we navigate the ever-changing digital landscape, embracing emerging technologies in cybersecurity is essential for staying ahead of the curve. By leveraging AI, blockchain, quantum computing, biometric authentication, and robust IoT security practices, we can create a more secure and resilient digital future. However, it’s crucial to remain vigilant about the ethical implications of these advancements, ensuring that technology is used responsibly and ethically to protect individuals and organizations alike.
Emerging technologies in cybersecurity, like AI and machine learning, are constantly evolving, and it’s important to stay ahead of the curve. This includes understanding how these technologies are being applied in other areas, like automotive. For instance, the choice between an Atlas SEL and SE can be influenced by the technology features offered, as detailed in this comparison.
Understanding these trends can help us better anticipate and address the cybersecurity challenges of the future.