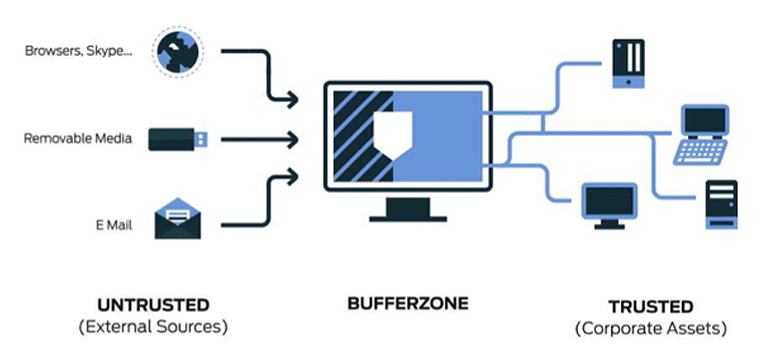
Emerging Technologies in Cybersecurity – C844
Emerging Technologies in Cybersecurity – C844 sets the stage for this enthralling narrative, offering readers a glimpse into a story that is rich in detail and brimming with originality from […]
Emerging Technologies in Cybersecurity – C844 sets the stage for this enthralling narrative, offering readers a glimpse into a story that is rich in detail and brimming with originality from the outset. The world of cybersecurity is constantly evolving, with new technologies emerging to address the ever-growing threat landscape. This exploration delves into the fascinating realm of these cutting-edge technologies, revealing their potential to revolutionize how we protect ourselves from cyberattacks.
From the intelligent algorithms of artificial intelligence to the robust security of blockchain, these emerging technologies are shaping the future of cybersecurity. This journey will examine the diverse ways these technologies are being used to enhance security, prevent breaches, and safeguard our digital world. We will explore the advantages and challenges associated with each technology, offering a comprehensive understanding of their impact on the evolving cybersecurity landscape.
Artificial Intelligence (AI) in Cybersecurity

AI is revolutionizing cybersecurity by offering innovative solutions to combat evolving cyber threats. AI algorithms can analyze vast amounts of data, identify patterns, and detect anomalies that might indicate malicious activity, enabling proactive threat detection and prevention.
AI Algorithms for Threat Detection and Prevention
AI algorithms can be used to detect and prevent cyberattacks by analyzing network traffic, user behavior, and system logs for suspicious patterns. These algorithms learn from past attacks and identify potential threats based on their characteristics. For instance, AI can analyze network traffic to identify unusual communication patterns, such as an influx of requests from unfamiliar IP addresses or unusual data transfer volumes, which could indicate a denial-of-service attack.
Benefits and Risks of Using AI in Cybersecurity
Benefits of AI in Cybersecurity
AI offers several benefits in cybersecurity, including:
- Enhanced Threat Detection: AI algorithms can analyze massive datasets, identify subtle anomalies, and detect threats that might be missed by human analysts. This proactive approach helps organizations stay ahead of cyberattacks.
- Improved Response Times: AI-powered systems can automate threat detection and response processes, enabling faster and more efficient responses to cyberattacks. This reduces the time it takes to contain an attack and minimize damage.
- Reduced False Positives: AI algorithms can learn from past incidents and refine their threat detection capabilities, reducing the number of false alarms and improving the accuracy of security alerts.
- Increased Efficiency: AI can automate repetitive tasks, freeing up security professionals to focus on more strategic and complex security initiatives.
Risks of Using AI in Cybersecurity
While AI offers significant advantages in cybersecurity, there are also potential risks to consider:
- Data Bias: AI algorithms are trained on existing data, which may contain biases that can lead to inaccurate or discriminatory outcomes. This can result in biased threat detection and response decisions.
- Adversarial Attacks: Attackers can manipulate AI systems by introducing malicious data or adversarial examples, causing them to misinterpret information and make incorrect decisions.
- Lack of Transparency: AI algorithms can be complex and opaque, making it difficult to understand how they arrive at their decisions. This lack of transparency can hinder trust and accountability in AI-powered security systems.
AI-Powered Cybersecurity Tools
Several AI-powered cybersecurity tools are available, offering various functionalities:
- Threat Intelligence Platforms: These platforms use AI to collect, analyze, and correlate threat intelligence data from various sources, providing insights into emerging threats and attack trends.
- Endpoint Security Solutions: AI-powered endpoint security solutions use machine learning to detect and prevent malware, ransomware, and other threats on devices. They can analyze user behavior and file activity to identify suspicious actions and block malicious software.
- Network Security Monitoring Tools: AI-powered network security monitoring tools analyze network traffic for anomalies and suspicious activity. They can identify denial-of-service attacks, data exfiltration attempts, and other network-based threats.
- Security Information and Event Management (SIEM) Systems: AI-powered SIEM systems use machine learning to correlate security events and identify potential security incidents. They can analyze logs from various sources and detect patterns that indicate malicious activity.
Machine Learning (ML) for Threat Detection
Machine learning (ML) is transforming cybersecurity by empowering systems to automatically detect and respond to threats that might otherwise go unnoticed. ML algorithms can analyze vast amounts of data, identifying patterns and anomalies that indicate malicious activity. This capability is particularly valuable in today’s threat landscape, where attackers constantly evolve their tactics and deploy new zero-day exploits.
Types of ML Models Used in Cybersecurity
ML models are categorized based on their learning approach and how they are trained. These models are crucial for different aspects of cybersecurity, each offering unique benefits for threat detection and response.
- Supervised Learning: In supervised learning, the ML model is trained on a labeled dataset, where each data point is associated with a known outcome. For instance, a dataset could include network traffic logs labeled as either malicious or benign. The model learns to identify patterns that distinguish malicious traffic from legitimate traffic. This approach is effective for detecting known threats and patterns.
- Unsupervised Learning: Unsupervised learning involves training models on unlabeled data, allowing the model to identify patterns and anomalies without prior knowledge of the outcome. This approach is particularly useful for detecting unknown threats and outliers that might not be captured by supervised learning models. For example, an unsupervised learning model could identify unusual network traffic patterns or user behavior deviations that could indicate a potential attack.
- Reinforcement Learning: Reinforcement learning trains models to learn through trial and error, receiving feedback for each action taken. The model learns to optimize its actions to achieve a desired outcome. In cybersecurity, this approach can be used to develop automated systems that can adapt to evolving threats and learn from their experiences. For instance, a reinforcement learning model could be trained to dynamically adjust security policies based on the changing threat landscape.
ML for Zero-Day Exploit Detection
Consider a scenario where a new zero-day exploit targeting a specific software vulnerability is unleashed. Traditional security solutions might not be able to detect this exploit immediately, as they rely on signatures for known threats. However, an ML-powered security system can detect this exploit in real-time by analyzing network traffic and user behavior for unusual patterns.
- The ML model, trained on historical data, can identify anomalies in network traffic patterns, such as unusual communication patterns or sudden spikes in data transfer.
- The model can also analyze user behavior for deviations from their typical activity, such as accessing unusual files or executing unexpected commands.
- Based on these anomalies, the ML model can trigger an alert, allowing security teams to investigate and respond to the zero-day exploit before it causes significant damage.
Blockchain Technology for Secure Data Management
Blockchain technology has emerged as a transformative force in cybersecurity, offering unparalleled security and transparency for data management. Its decentralized and immutable nature makes it an ideal solution for safeguarding sensitive information in a world increasingly vulnerable to cyber threats.
Blockchain’s Role in Enhancing Data Security and Integrity
Blockchain technology significantly enhances data security and integrity by implementing a decentralized, tamper-proof ledger. Each transaction or data update is recorded in a block, which is then cryptographically linked to previous blocks, creating an immutable chain. This chain of blocks is distributed across multiple nodes in the network, making it extremely difficult for any single entity to alter or corrupt the data.
- Immutability: Once a block is added to the blockchain, it cannot be altered or deleted, ensuring data integrity and accountability. Any attempt to modify the data would be immediately detectable, creating a verifiable audit trail.
- Transparency: All transactions and data updates are recorded on the blockchain, making them visible to all participants. This transparency fosters trust and accountability, as everyone can track the history of data changes.
- Decentralization: The blockchain is not controlled by any single entity, making it resistant to attacks and manipulation. The distributed nature of the ledger ensures that data is not stored in a single location, reducing the risk of data breaches.
Blockchain’s Role in Secure Identity Management and Access Control
Blockchain technology can revolutionize identity management and access control by providing a secure and verifiable platform for identity verification and authorization.
- Digital Identity: Blockchain can serve as a decentralized platform for storing and managing digital identities. Users can control their own identity data and grant access to specific information to authorized parties, enhancing privacy and security.
- Access Control: Blockchain can facilitate secure access control by creating a system where users can grant or revoke access to data based on predefined rules and permissions. This eliminates the need for centralized authorities and reduces the risk of unauthorized access.
- Secure Authentication: Blockchain can be used to implement secure authentication mechanisms, such as multi-factor authentication (MFA) and biometrics, to verify user identities and prevent unauthorized access.
Comparison of Traditional Data Management Methods with Blockchain-Based Solutions
| Feature | Traditional Data Management | Blockchain-Based Solutions |
|---|---|---|
| Security | Vulnerable to data breaches, manipulation, and unauthorized access | Highly secure due to immutability, decentralization, and cryptography |
| Transparency | Limited transparency, often controlled by a central authority | Transparent and auditable, with all transactions recorded on the blockchain |
| Immutability | Data can be easily altered or deleted | Immutable data, ensuring integrity and accountability |
Quantum Computing and Cybersecurity
The advent of quantum computing presents both exciting opportunities and significant challenges for cybersecurity. Its unique capabilities, particularly in processing and breaking complex algorithms, could revolutionize how we secure data and systems. Understanding the potential impact of quantum computing on current cryptographic methods and exploring emerging quantum-resistant cryptography techniques is crucial for maintaining a secure digital landscape.
Quantum Computing’s Impact on Cryptography
Quantum computers leverage the principles of quantum mechanics, enabling them to perform computations in ways that are impossible for classical computers. This power holds significant implications for cryptography, particularly for public-key cryptography, which underpins many of our online security protocols.
- Breaking Public-Key Cryptography: Quantum computers, using algorithms like Shor’s algorithm, can efficiently factor large numbers, a task that is computationally infeasible for classical computers. This poses a direct threat to commonly used public-key cryptosystems, such as RSA and ECC, which rely on the difficulty of factoring large numbers.
- Implications for Digital Security: The potential compromise of public-key cryptography would have far-reaching consequences for online security. Sensitive information, including financial transactions, digital signatures, and confidential communications, could become vulnerable to attacks from quantum computers.
Quantum-Resistant Cryptography
In response to the threat posed by quantum computing, researchers are actively developing quantum-resistant cryptography (QRC), also known as post-quantum cryptography. These algorithms are designed to be secure against attacks from both classical and quantum computers.
- Lattice-Based Cryptography: This approach relies on the mathematical properties of lattices, which are complex structures in high-dimensional spaces. Lattice-based cryptosystems offer strong security guarantees and are considered promising candidates for QRC.
- Code-Based Cryptography: This method leverages error-correcting codes, which are used to detect and correct errors in data transmission. Code-based cryptosystems are known for their resistance to attacks from both classical and quantum computers.
- Hash-Based Cryptography: Hash functions are mathematical algorithms that generate a unique “fingerprint” for a given input. Hash-based cryptography uses these fingerprints for digital signatures and other security applications.
- Multivariate Cryptography: This approach relies on the difficulty of solving systems of multivariate polynomial equations. Multivariate cryptosystems are considered to be resistant to attacks from quantum computers.
Visual Representation of Classical and Quantum Computing
Image Description: The image would depict two separate diagrams, representing classical and quantum computing. The classical diagram would showcase a typical computer architecture with central processing units (CPUs), memory, and storage, illustrating the sequential processing of bits. The quantum diagram would highlight the concept of qubits, superposition, and entanglement, showcasing the parallel processing capabilities of quantum computers.
The image would then depict the impact of these computing paradigms on cryptography. The classical cryptography section would showcase the traditional encryption methods, such as RSA, ECC, and AES, highlighting their reliance on computational complexity for security. The quantum cryptography section would illustrate the emergence of quantum-resistant algorithms, such as lattice-based, code-based, and hash-based cryptography, showcasing their resilience against quantum attacks.
The image would visually emphasize the significant difference between classical and quantum computing, highlighting their respective strengths and weaknesses in cryptography. It would provide a clear and intuitive understanding of the evolving landscape of cybersecurity in the era of quantum computing.
Biometric Authentication: Emerging Technologies In Cybersecurity – C844
Biometric authentication leverages unique biological traits to verify identities, offering a robust and secure alternative to traditional methods like passwords. This approach utilizes distinctive physical characteristics, such as fingerprints, facial features, or iris patterns, to authenticate users. It enhances security by making it significantly more difficult for unauthorized individuals to gain access to sensitive systems or data.
Different Biometric Authentication Methods
Biometric authentication encompasses a range of methods, each employing distinct biological traits for identification.
- Facial Recognition: This method analyzes facial features, including the distance between eyes, the shape of the nose, and the contour of the jawline, to identify individuals. It is widely used in smartphones, access control systems, and law enforcement.
- Fingerprint Scanning: Fingerprint scanning relies on the unique patterns and ridges on an individual’s fingertips for identification. This method is commonly used in smartphones, laptops, and security systems.
- Iris Scanning: Iris scanning uses the intricate patterns in the iris, the colored part of the eye, for authentication. This method offers high accuracy and is employed in secure environments like government buildings and data centers.
- Voice Recognition: This method analyzes the unique characteristics of a person’s voice, including pitch, tone, and rhythm, to verify their identity. It is frequently used in voice assistants, banking applications, and call center authentication.
- Hand Geometry: Hand geometry scans measure the shape and size of an individual’s hand, including the length of fingers and the width of the palm, for authentication. This method is commonly used in access control systems and time and attendance tracking.
Security and Privacy Implications of Biometric Authentication
Biometric authentication offers significant advantages in security and convenience, but it also presents privacy concerns that must be carefully considered.
- Security: Biometric authentication enhances security by making it significantly more difficult for unauthorized individuals to gain access to sensitive systems or data. It is more difficult to forge or steal biometric data compared to passwords or other traditional authentication methods.
- Privacy: The collection and storage of biometric data raise privacy concerns. Unauthorized access to this data could lead to identity theft or other security breaches. It is crucial to ensure that biometric data is collected, stored, and used responsibly and securely.
- Accuracy: Biometric authentication systems can be susceptible to errors, such as false positives (identifying an unauthorized individual as authorized) or false negatives (failing to identify an authorized individual). These errors can lead to security breaches or inconvenience for legitimate users.
- Data Security: It is crucial to ensure that biometric data is securely stored and protected from unauthorized access. Data breaches involving biometric data can have serious consequences for individuals and organizations.
Examples of Biometric Authentication in Various Sectors
Biometric authentication is increasingly used in various sectors to enhance security and improve user experience.
- Banking: Banks use biometric authentication for online banking, ATM transactions, and mobile payments. This helps prevent fraud and unauthorized access to accounts.
- Healthcare: Hospitals and clinics use biometric authentication to verify patient identities, control access to medical records, and ensure the accuracy of medication dispensing.
- Government: Government agencies use biometric authentication for passport and visa applications, voter registration, and access control to sensitive facilities.
- Education: Schools and universities use biometric authentication for student attendance, library access, and secure access to online learning platforms.
- Retail: Retailers use biometric authentication for loyalty programs, personalized promotions, and contactless payments.
Cloud Security and Emerging Technologies

The cloud has revolutionized how businesses operate, offering scalability, flexibility, and cost-effectiveness. However, this shift also brings unique security challenges that require careful consideration and robust mitigation strategies. This section explores the security concerns specific to cloud environments and examines how emerging technologies are shaping the landscape of cloud security.
Cloud Security Challenges, Emerging technologies in cybersecurity – c844
Cloud computing introduces a unique set of security challenges due to the shared responsibility model between cloud providers and users. The shared responsibility model means that both parties are responsible for securing their respective parts of the cloud environment. While cloud providers are responsible for securing the underlying infrastructure, users are responsible for securing their data, applications, and configurations within the cloud.
- Data Security and Privacy: Data breaches in the cloud can have severe consequences, leading to financial losses, reputational damage, and legal repercussions. Ensuring data confidentiality, integrity, and availability is crucial in cloud environments. Cloud providers offer various security tools and services, such as encryption, access controls, and data masking, to help protect sensitive information. However, users also play a vital role in implementing appropriate security measures, such as strong passwords, multi-factor authentication, and data encryption at rest and in transit.
- Misconfiguration and Compliance: Misconfigurations in cloud environments can expose sensitive data and applications to vulnerabilities. Organizations need to implement robust security configurations, ensure compliance with relevant regulations, and continuously monitor their cloud environments for misconfigurations. Cloud security tools can help automate configuration management and compliance monitoring, reducing the risk of misconfigurations.
- Third-Party Risks: Cloud environments often rely on third-party services and applications, introducing additional security risks. Organizations need to carefully vet third-party providers, assess their security practices, and implement appropriate security controls to mitigate potential risks. Cloud security tools can help organizations manage and monitor third-party risks.
- Cloud Security Posture Management: Maintaining a strong cloud security posture requires continuous monitoring and assessment of security risks. Organizations need to identify vulnerabilities, track security incidents, and implement corrective measures. Cloud security tools provide comprehensive visibility into cloud environments, enabling organizations to proactively manage their security posture.
The Future of Cybersecurity
The future of cybersecurity is rapidly evolving, driven by the relentless advancement of technology and the ever-increasing sophistication of cyberattacks. Emerging technologies are playing a pivotal role in shaping this landscape, offering both opportunities and challenges for cybersecurity professionals.
Emerging Technologies and Their Impact on Cybersecurity
The integration of emerging technologies into cybersecurity is transforming the way we approach threat detection, prevention, and response. These technologies are not only enhancing existing security measures but also creating new avenues for innovation and defense.
- Artificial Intelligence (AI) and Machine Learning (ML): AI and ML are revolutionizing threat detection and response by automating the analysis of vast amounts of data to identify patterns and anomalies that might indicate malicious activity. AI-powered security systems can learn from past attacks and adapt to new threats, making them more effective at detecting and responding to cyberattacks. For example, AI can analyze network traffic to identify suspicious patterns, detect malware before it infects systems, and even predict potential attacks based on historical data.
- Blockchain Technology: Blockchain technology offers a secure and transparent way to manage data, making it an ideal solution for protecting sensitive information. Its decentralized nature makes it resistant to tampering and data breaches, ensuring the integrity of data and transactions. In cybersecurity, blockchain can be used to secure digital identities, authenticate users, and protect sensitive data.
- Quantum Computing: Quantum computing has the potential to revolutionize cybersecurity by breaking current encryption methods, but it also offers new opportunities for building more secure systems. Quantum computers can perform calculations at speeds that are impossible for traditional computers, making them capable of cracking complex encryption algorithms that currently protect sensitive data. However, quantum computing can also be used to develop new encryption methods that are resistant to quantum attacks.
- Biometric Authentication: Biometric authentication, using unique biological traits for identification, is becoming increasingly popular as a secure and convenient way to verify user identities. Biometric authentication can be used to secure access to sensitive data and systems, making it more difficult for unauthorized individuals to gain access.
- Cloud Security: Cloud computing has become ubiquitous, but it also presents new security challenges. Cloud security solutions are evolving to address these challenges, offering advanced protection for data and applications stored in the cloud.
Potential Impact of Emerging Technologies on Cyberattacks and Defenses
The impact of emerging technologies on cyberattacks and defenses is multifaceted. While some technologies can be used to enhance security measures, others can be exploited by attackers to launch more sophisticated and destructive attacks.
- Enhanced Threat Detection and Response: AI and ML can significantly enhance threat detection and response capabilities by automating the analysis of large datasets, identifying patterns, and predicting potential attacks. This allows security teams to respond to threats more quickly and effectively.
- New Attack Vectors: Emerging technologies can also create new attack vectors for cybercriminals. For example, quantum computers could be used to break current encryption methods, making sensitive data vulnerable to attacks. Attackers could also use AI and ML to develop more sophisticated phishing campaigns and malware.
- Increased Complexity: The rapid adoption of emerging technologies is increasing the complexity of cybersecurity landscapes. This can make it challenging for security teams to keep up with the latest threats and vulnerabilities.
- Need for Skilled Professionals: The growing reliance on emerging technologies requires cybersecurity professionals with specialized skills in AI, ML, blockchain, and other technologies.
Emerging Technologies with Significant Impact on Cybersecurity
Several emerging technologies are poised to have a significant impact on cybersecurity in the coming years:
- Zero-Trust Security: Zero-trust security models assume that no user or device can be trusted by default. This approach emphasizes continuous verification and authentication, reducing the risk of unauthorized access.
- Software-Defined Networking (SDN): SDN provides a more flexible and programmable way to manage network infrastructure, making it easier to implement security policies and detect anomalies.
- Internet of Things (IoT) Security: The proliferation of IoT devices presents new security challenges. Secure by design principles and advanced security solutions are crucial for protecting IoT devices and the data they collect.
- Edge Computing: Edge computing brings data processing closer to the user, reducing latency and improving performance. Secure edge computing solutions are essential to protect data and applications at the edge.
- 5G Security: 5G networks offer faster speeds and lower latency, but they also introduce new security risks. Secure 5G networks are essential to protect data and communications from cyberattacks.
Concluding Remarks
As we conclude this exploration of emerging technologies in cybersecurity, it becomes evident that the future of online security is intricately linked to the adoption and advancement of these innovative solutions. From the sophisticated defenses of AI to the decentralized security of blockchain, these technologies are poised to transform the way we approach cybersecurity, ultimately making the digital world a safer place for individuals and organizations alike. The continuous evolution of these technologies ensures a dynamic and challenging landscape, demanding ongoing adaptation and innovation to stay ahead of emerging threats. It is through this ongoing commitment to innovation that we can build a more resilient and secure digital future.
Emerging technologies in cybersecurity, like AI-powered threat detection, are constantly evolving to stay ahead of cybercriminals. However, securing data isn’t just a concern for tech giants; it’s crucial for businesses of all sizes, even restaurants. A restaurant technology consultant can help implement security measures for POS systems and customer data, ensuring a safe and secure dining experience.
As the digital landscape continues to change, businesses need to stay informed about emerging cybersecurity threats and invest in the right solutions to protect themselves.