Criminal Technology: A History of Innovation and Crime
Criminal technology, a fascinating intersection of innovation and illicit activity, has evolved alongside society, mirroring its advancements and exploiting its vulnerabilities. From the rudimentary tools of past centuries to the […]

Criminal technology, a fascinating intersection of innovation and illicit activity, has evolved alongside society, mirroring its advancements and exploiting its vulnerabilities. From the rudimentary tools of past centuries to the sophisticated cyberweapons of today, criminals have continuously adapted to new technologies, pushing the boundaries of what’s possible.
This exploration delves into the historical evolution of criminal technology, examining the various types, their applications in crime, and the impact they have on law enforcement, society, and our ethical considerations. We’ll also explore future trends and the potential challenges they present.
Evolution of Criminal Technology

The evolution of criminal technology mirrors the advancement of technology itself, with criminals adapting and exploiting new tools and methods to achieve their objectives. From the rudimentary tools of the past to the sophisticated techniques of the modern era, the history of criminal technology reveals a fascinating interplay between innovation and criminal intent.
Traditional Criminal Technology
Traditional criminal technology encompasses the tools and methods employed by criminals before the advent of modern technology. These methods often relied on physical prowess, deception, and basic tools.
- Lockpicking and Burglary Tools: Criminals have long employed tools like lockpicks, crowbars, and other implements to gain unauthorized entry into buildings. These tools were often handmade and required a degree of skill and knowledge to use effectively. For instance, the “skeleton key” – a simple, flat key that could open many locks – was a common tool used by burglars in the past.
- Forged Documents and Identity Theft: Historically, criminals have used forged documents to assume false identities or to create false documentation for various illicit activities. This could include creating fake passports, driver’s licenses, or other official documents to deceive authorities and facilitate criminal activities.
- Weaponry: Traditional criminal technology also includes the use of weapons. While weapons like knives, clubs, and firearms have existed for centuries, their development and use have evolved over time. For example, the development of the firearm led to a significant increase in the lethality of crime and the use of firearms in robberies and other violent crimes.
The Rise of Modern Criminal Technology
The 20th and 21st centuries have witnessed a dramatic shift in the nature of criminal technology, with the widespread adoption of computers, the internet, and mobile devices. This technological revolution has provided criminals with new tools and methods for committing crimes, often with a higher degree of sophistication and anonymity.
- Cybercrime: The rise of the internet has led to a surge in cybercrime, including hacking, phishing, malware distribution, and identity theft. Criminals can now exploit vulnerabilities in computer systems and networks to steal sensitive information, disrupt services, or extort money from individuals and organizations.
- Financial Crimes: The digitalization of financial systems has created new opportunities for financial crimes, such as money laundering, credit card fraud, and online scams. Criminals can use sophisticated techniques to move money across borders, create fake identities, and manipulate financial transactions.
- Digital Forensics: As criminal technology has become more sophisticated, law enforcement agencies have developed advanced tools and techniques for digital forensics. These techniques allow investigators to analyze digital evidence, such as computer files, emails, and social media data, to track down criminals and build cases.
Types of Criminal Technology

Criminal technology encompasses a wide range of tools and techniques employed by individuals or groups to commit crimes. This technology can range from simple everyday objects to sophisticated devices specifically designed for criminal activities. Understanding the types of criminal technology and their applications is crucial for law enforcement agencies, cybersecurity professionals, and the public at large to mitigate risks and prevent criminal acts.
Types of Criminal Technology
The following table categorizes various types of criminal technology based on their functionalities and applications:
| Type of Technology | Examples | Applications in Crime | Impact on Society |
|---|---|---|---|
| Communication Technologies | Cell phones, internet, social media, encrypted messaging apps | Coordinated criminal activities, recruitment, planning, dissemination of propaganda, communication with accomplices, intimidation, harassment, stalking, fraud, identity theft, money laundering | Increased anonymity and ease of communication for criminals, challenges for law enforcement in monitoring and intercepting communications, potential for misuse and exploitation of technology for malicious purposes |
| Financial Technologies | Credit cards, debit cards, online banking, cryptocurrency, digital wallets | Financial fraud, money laundering, identity theft, ransomware, extortion, cyberattacks on financial institutions | Increased vulnerability to financial crimes, potential for economic instability, challenges in tracking and regulating financial transactions, rise of cybercrime and financial terrorism |
| Surveillance Technologies | Hidden cameras, drones, GPS trackers, facial recognition software, surveillance software | Surveillance, monitoring, stalking, identity theft, blackmail, extortion, theft, illegal recording, data breaches | Privacy concerns, potential for misuse by governments and private entities, increased surveillance and erosion of personal freedom, potential for mass surveillance and social control |
| Weapon Technologies | Firearms, explosives, chemical weapons, biological weapons, cyberweapons | Violence, intimidation, terrorism, mass casualty events, disruption of critical infrastructure, cyberattacks on critical systems | Increased risk of violence and terrorism, potential for mass casualties, social unrest, economic disruption, geopolitical instability, threats to national security |
| Information Technologies | Computers, laptops, tablets, smartphones, servers, networks, databases, software | Cybercrime, hacking, data breaches, malware, phishing, ransomware, denial-of-service attacks, identity theft, fraud, espionage | Increased vulnerability to cybercrime, disruption of critical infrastructure, economic losses, erosion of trust in digital systems, potential for information warfare and manipulation |
Impact of Criminal Technology on Law Enforcement

The rise of criminal technology has posed significant challenges for law enforcement agencies worldwide. As criminals leverage advanced tools and techniques to commit crimes, law enforcement must adapt and evolve to effectively combat these threats. This section explores the impact of criminal technology on law enforcement, examining the challenges it presents, the influence on investigative techniques, and the ways in which law enforcement is utilizing technology to counter criminal activity.
Challenges Faced by Law Enforcement, Criminal technology
The increasing sophistication of criminal technology presents numerous challenges for law enforcement agencies. These challenges stem from the rapidly evolving nature of criminal techniques, the difficulty in keeping pace with technological advancements, and the need to balance security with privacy concerns.
- Rapidly Evolving Criminal Techniques: Criminals are constantly innovating and adapting their methods, leveraging new technologies to commit crimes with greater efficiency and anonymity. This rapid evolution makes it difficult for law enforcement to stay ahead of the curve and develop effective countermeasures.
- Difficulty in Keeping Pace with Technological Advancements: The rapid pace of technological development poses a significant challenge for law enforcement agencies. Maintaining expertise in the latest technologies and adapting investigative techniques to new platforms requires substantial resources and ongoing training.
- Balancing Security with Privacy Concerns: The use of technology to combat crime raises important ethical and legal considerations regarding privacy. Law enforcement agencies must strike a delicate balance between ensuring public safety and respecting individual privacy rights. This requires careful consideration of surveillance techniques, data collection practices, and the legal frameworks governing these activities.
Influence on Investigative Techniques
Criminal technology has significantly influenced the development of new investigative techniques and strategies. Law enforcement agencies are increasingly relying on technological tools and data analysis to gather evidence, identify suspects, and disrupt criminal networks.
- Digital Forensics: The rise of digital evidence has led to the development of specialized forensic techniques for examining computers, mobile devices, and other digital platforms. Digital forensics plays a crucial role in gathering evidence, reconstructing events, and identifying perpetrators.
- Data Analytics and Predictive Policing: Law enforcement agencies are leveraging data analytics to identify patterns in criminal activity, predict crime hotspots, and allocate resources effectively. Predictive policing models use historical data to forecast future crime trends, allowing for proactive crime prevention strategies.
- Cybersecurity and Cybercrime Investigations: The increasing prevalence of cybercrime has led to the development of specialized units and techniques for investigating online criminal activity. These units focus on identifying cybercriminals, tracing digital footprints, and disrupting malicious networks.
Utilization of Technology to Combat Crime
Law enforcement agencies are utilizing a wide range of technologies to combat crime, from traditional surveillance tools to advanced data analysis platforms. These technologies enhance investigative capabilities, improve communication and coordination, and support crime prevention efforts.
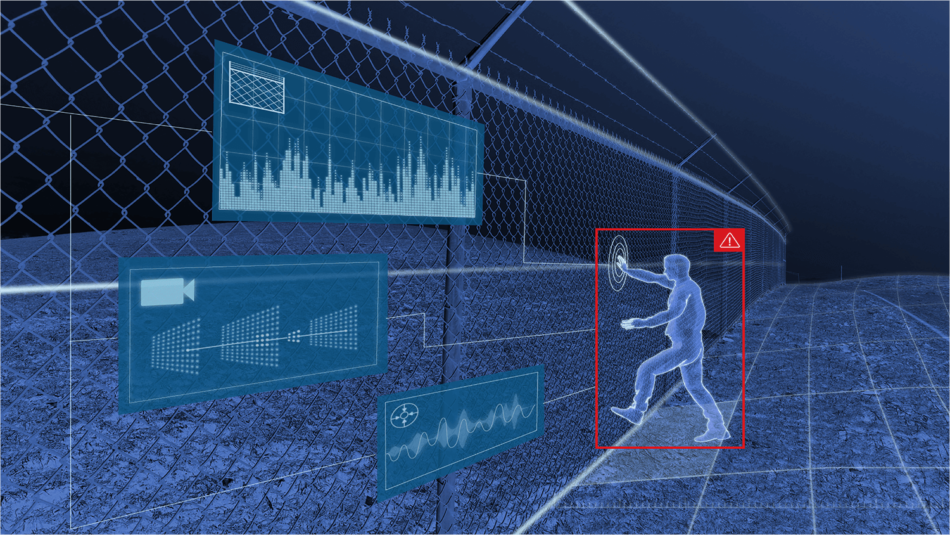
- Surveillance Technologies: Law enforcement agencies use surveillance technologies such as CCTV cameras, drones, and body-worn cameras to monitor public spaces, gather evidence, and track suspects. These technologies provide real-time situational awareness and enhance the effectiveness of investigations.
- Biometric Identification Systems: Biometric identification systems, such as facial recognition and fingerprint scanning, are used to verify identities, identify suspects, and track individuals. These technologies can assist in crime investigations, border security, and public safety.
- Communication and Collaboration Tools: Law enforcement agencies rely on communication and collaboration tools, such as secure messaging platforms and data-sharing systems, to facilitate information exchange, coordinate operations, and improve communication between agencies.
Ethical and Legal Considerations
The advancement of criminal technology, while offering powerful tools for law enforcement, raises significant ethical and legal concerns. These technologies, capable of collecting vast amounts of data, tracking individuals, and accessing sensitive information, necessitate careful consideration of their impact on privacy, surveillance, and civil liberties.
Privacy Violations
The use of criminal technology can potentially infringe on individual privacy rights. Facial recognition systems, for instance, can identify individuals in public spaces without their consent, raising concerns about the potential for misuse and the erosion of privacy. Similarly, data mining techniques used by law enforcement agencies can gather vast amounts of personal information, including browsing history, social media activity, and financial transactions, without individuals’ knowledge or explicit permission. This raises concerns about the potential for profiling and discrimination based on personal data.
Surveillance and Data Collection
Criminal technology often involves the use of surveillance technologies, such as body cameras, drones, and facial recognition systems, which can monitor individuals’ activities in real-time. While these technologies can be beneficial in crime prevention and investigation, they also raise concerns about excessive surveillance and the potential for abuse. The collection and storage of vast amounts of data raise concerns about data breaches and the misuse of sensitive information.
Access to Sensitive Information
Criminal technology can provide law enforcement agencies with access to sensitive information, such as medical records, financial data, and communications. This access raises concerns about the potential for misuse, unauthorized disclosure, and the violation of individual privacy.
Regulation and Ethical Frameworks
The ethical and legal implications of criminal technology necessitate the development of robust regulations and ethical frameworks to govern their use. These frameworks should ensure that the use of criminal technology is proportionate, necessary, and respects individual rights. They should also address issues such as data privacy, transparency, accountability, and oversight.
Future Trends in Criminal Technology
The landscape of criminal technology is constantly evolving, driven by rapid advancements in artificial intelligence, biotechnology, and other cutting-edge fields. This evolution presents both exciting opportunities for law enforcement and concerning possibilities for malicious actors. Understanding these trends is crucial for developing proactive strategies to mitigate the risks and ensure a safe future.
Potential Advancements in Criminal Technology
The future of criminal technology is likely to be characterized by the convergence of existing technologies and the emergence of entirely new ones. This convergence will create sophisticated tools that can be used for both legitimate and illicit purposes.
- Artificial Intelligence (AI): AI is poised to revolutionize various aspects of crime prevention and detection. For example, AI-powered surveillance systems can analyze vast amounts of data to identify potential threats, predict criminal activity, and optimize resource allocation. However, AI can also be used by criminals to create more sophisticated phishing attacks, generate realistic deepfakes for fraud, and automate the spread of misinformation.
- Biotechnology: Advancements in biotechnology, particularly in areas like gene editing and synthetic biology, raise significant ethical and security concerns. For instance, criminals could exploit these technologies to create bioweapons or modify organisms to cause environmental damage. Furthermore, genetic information could be misused for identity theft or blackmail.
- Internet of Things (IoT): The increasing interconnectedness of devices through the IoT presents both opportunities and vulnerabilities. Criminals could exploit security flaws in IoT devices to launch distributed denial-of-service attacks, steal personal data, or control critical infrastructure. However, IoT devices can also be used for crime prevention by providing real-time data and enabling remote monitoring.
- Cyber Warfare: The lines between traditional warfare and cyberwarfare are blurring. Nations and non-state actors are increasingly using cyberattacks to disrupt critical infrastructure, steal sensitive information, and influence political events. These attacks can have devastating consequences for individuals, businesses, and entire countries.
Emerging Technologies for Criminal Exploitation
While some technologies are already being exploited for criminal purposes, others are still in their nascent stages but hold significant potential for misuse.
- Quantum Computing: Quantum computers are expected to revolutionize fields like cryptography and drug discovery. However, their immense computational power could also be used by criminals to crack encryption algorithms currently used to secure sensitive data, rendering existing security measures obsolete.
- Brain-Computer Interfaces (BCIs): BCIs allow individuals to control devices with their thoughts. While promising for medical applications, BCIs also raise concerns about privacy and security. Criminals could potentially exploit BCIs to steal thoughts, manipulate behavior, or even control individuals remotely.
- Synthetic Biology: Synthetic biology allows scientists to design and build biological systems from scratch. This technology could be used for beneficial purposes, such as creating new drugs or biofuels. However, it could also be used by criminals to create dangerous pathogens or modify organisms for malicious purposes.
Strategies for Mitigating Risks
To effectively address the challenges posed by future criminal technology, proactive measures are essential.
- Invest in Research and Development: Continued investment in research and development is crucial for staying ahead of emerging threats. This includes developing new technologies to counter criminal activity, enhancing cybersecurity measures, and understanding the ethical implications of emerging technologies.
- Foster Collaboration: Effective collaboration between law enforcement agencies, private sector companies, and academic institutions is essential for sharing information, developing best practices, and coordinating responses to evolving threats.
- Promote Ethical Considerations: The development and deployment of criminal technologies must be guided by ethical principles. This includes ensuring transparency, accountability, and respect for human rights. It also requires addressing potential biases in AI systems and ensuring that technology is used responsibly.
- Educate the Public: Raising public awareness about the risks associated with criminal technology is crucial for preventing crime and fostering responsible use of technology. This includes educating individuals about cybersecurity best practices, recognizing potential scams, and reporting suspicious activity.
Ultimate Conclusion: Criminal Technology
The constant interplay between criminal technology and law enforcement is a dynamic and evolving landscape. As technology advances, so too will the methods used to exploit it for criminal purposes. It is imperative that we stay informed, adapt our strategies, and implement ethical frameworks to ensure that the benefits of technology outweigh the risks.
Criminal technology is constantly evolving, from sophisticated hacking tools to advanced surveillance systems. But even in the world of crime, technology can be used for good. For example, survey technology can be used to collect data on criminal activity, helping law enforcement agencies to better understand trends and develop strategies for prevention.
This data can then be used to improve security measures and ultimately help to reduce crime rates.