CA Technologies Identity Management: Securing the Modern Enterprise
CA Technologies Identity Management is a comprehensive suite of solutions designed to address the ever-evolving security landscape of today’s organizations. It empowers businesses to manage user identities and access rights […]
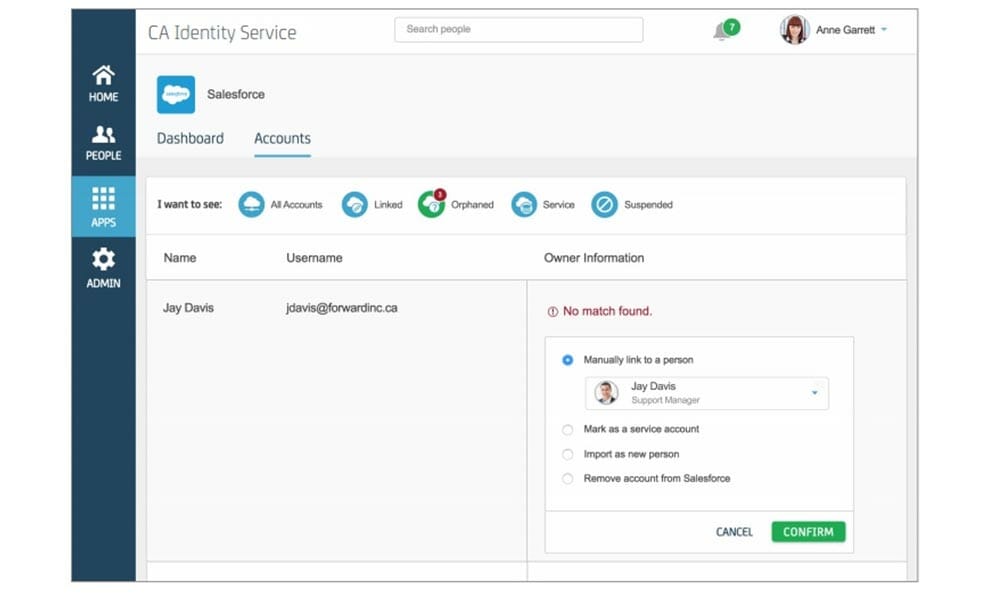
CA Technologies Identity Management is a comprehensive suite of solutions designed to address the ever-evolving security landscape of today’s organizations. It empowers businesses to manage user identities and access rights across various systems and applications, ensuring secure and compliant operations.
From single sign-on (SSO) to multi-factor authentication (MFA), CA Technologies provides a robust framework for controlling access and mitigating risks. Its solutions are built to adapt to modern security challenges, including cloud adoption, mobile device proliferation, and the growing threat of identity theft.
Benefits of Implementing CA Technologies Identity Management

Implementing CA Technologies identity management solutions can bring significant benefits to organizations of all sizes. These solutions provide a comprehensive approach to managing user identities and access, helping organizations improve security, enhance productivity, and reduce costs.
Enhanced Security and Compliance
CA Technologies identity management solutions help organizations achieve a higher level of security and compliance by providing a centralized platform for managing user identities and access.
- Stronger Authentication: By implementing multi-factor authentication (MFA), organizations can significantly reduce the risk of unauthorized access. MFA requires users to provide multiple forms of authentication, such as a password and a one-time code, making it much harder for attackers to gain access to sensitive data.
- Centralized Access Control: CA Technologies solutions provide a centralized platform for managing user access to applications, systems, and data. This allows organizations to define and enforce access policies based on roles, responsibilities, and security requirements. This helps ensure that only authorized users have access to the information they need.
- Compliance with Regulations: Organizations are required to comply with various regulations, such as GDPR and HIPAA, that govern the handling of sensitive data. CA Technologies identity management solutions help organizations meet these compliance requirements by providing features such as data masking, access auditing, and reporting.
Improved User Productivity and Efficiency
CA Technologies identity management solutions can improve user productivity and efficiency by simplifying the user experience and reducing the time it takes to access the resources they need.
- Self-Service Password Reset: Users can reset their passwords themselves, eliminating the need to contact IT support. This saves time and reduces the burden on IT staff.
- Single Sign-On (SSO): Users can access multiple applications with a single set of credentials. This eliminates the need to remember multiple passwords, improving user productivity and reducing the risk of forgotten passwords.
- Automated Provisioning and De-provisioning: User accounts can be automatically created and deleted as employees join and leave the organization. This eliminates manual processes and reduces the risk of security vulnerabilities.
Reduced Operational Costs
CA Technologies identity management solutions can help organizations reduce operational costs by automating tasks, improving efficiency, and reducing the risk of security incidents.
- Reduced IT Support Costs: By automating tasks such as password resets and user provisioning, organizations can reduce the workload on IT staff. This frees up IT staff to focus on more strategic initiatives.
- Reduced Security Incident Costs: By implementing strong security measures, such as MFA and access control, organizations can reduce the risk of security incidents. This helps organizations avoid the costs associated with data breaches, including legal fees, fines, and reputational damage.
- Improved Compliance Costs: CA Technologies identity management solutions help organizations meet compliance requirements, reducing the risk of fines and penalties.
Enhanced Risk Management, Ca technologies identity management
CA Technologies identity management solutions help organizations manage risk by providing visibility into user activity and enabling them to identify and respond to potential threats.
- Access Auditing and Reporting: Organizations can track user activity, including login attempts, access requests, and data modifications. This information can be used to identify potential security threats and investigate security incidents.
- Real-Time Threat Detection: CA Technologies identity management solutions can detect suspicious activity in real time, such as unusual login patterns or attempts to access sensitive data. This allows organizations to respond to threats quickly and effectively.
- Improved Incident Response: By providing a comprehensive view of user activity, CA Technologies identity management solutions help organizations respond to security incidents more effectively. This can help reduce the impact of incidents and minimize downtime.
Future Trends in CA Technologies Identity Management

The landscape of identity management is constantly evolving, driven by technological advancements and evolving security threats. CA Technologies is at the forefront of this evolution, adapting its solutions to meet the challenges and opportunities presented by emerging trends.
Zero Trust Security
Zero Trust security is a security framework that assumes no user or device can be trusted by default. This approach emphasizes continuous verification and authentication, regardless of location or device. CA Technologies is incorporating Zero Trust principles into its identity management solutions by:
- Enhancing access controls: CA Technologies is implementing granular access controls that allow organizations to define specific permissions for users and devices based on context, such as time of day, location, and device type.
- Integrating with threat intelligence platforms: CA Technologies is integrating its identity management solutions with threat intelligence platforms to detect and respond to malicious activity in real-time.
- Promoting multi-factor authentication (MFA): CA Technologies is advocating for the use of MFA, which requires users to provide multiple forms of authentication, such as a password and a one-time code, to access sensitive resources.
Cloud-Based Identity Management
Cloud-based identity management solutions offer scalability, flexibility, and cost-effectiveness. CA Technologies is leveraging the cloud to deliver its identity management solutions, providing organizations with:
- On-demand access: Cloud-based identity management solutions allow organizations to provision and manage user identities quickly and easily, without the need for complex infrastructure.
- Scalability and flexibility: Cloud-based solutions can scale to meet the needs of organizations of all sizes, and they can be easily adapted to changing business requirements.
- Cost savings: Cloud-based identity management solutions eliminate the need for expensive hardware and software, reducing overall costs.
Artificial Intelligence (AI) and Machine Learning (ML) in Identity Management
AI and ML are transforming identity management by automating tasks, improving security, and personalizing user experiences. CA Technologies is incorporating AI and ML into its solutions to:
- Automate user provisioning and deprovisioning: AI and ML can automate the process of creating, updating, and deleting user accounts, reducing administrative overhead.
- Detect and prevent fraud: AI and ML can analyze user behavior patterns to identify suspicious activity and prevent unauthorized access.
- Personalize user experiences: AI and ML can be used to personalize user interfaces and provide relevant access controls based on individual user needs.
Biometric Authentication
Biometric authentication uses unique biological characteristics, such as fingerprints, facial recognition, or iris scans, to verify user identity. CA Technologies is integrating biometric authentication into its identity management solutions to:
- Enhance security: Biometric authentication is more secure than traditional methods, such as passwords, as it is difficult to forge or steal biological characteristics.
- Improve user convenience: Biometric authentication is more convenient than traditional methods, as users do not need to remember passwords or carry physical tokens.
- Enable seamless access: Biometric authentication can be used to enable seamless access to applications and devices, enhancing user experience.
Summary

By implementing CA Technologies Identity Management, organizations can enhance security, streamline operations, and optimize user experiences. The platform’s flexibility and adaptability ensure it can be integrated seamlessly into existing IT infrastructure, providing a comprehensive and effective solution for managing user identities and access rights.
CA Technologies’ identity management solutions are crucial for securing access to sensitive data and applications. These solutions can be deployed in various environments, including cloud platforms, and companies like American Virtual Cloud Technologies Ireland can help organizations leverage these capabilities for optimal security and compliance.
By partnering with specialized cloud providers, businesses can ensure their identity management systems are integrated seamlessly into their overall cloud infrastructure, enabling a secure and efficient approach to user authentication and authorization.




