Perimeter Technology: Securing the Digital Frontier
Perimeter technology sets the stage for this enthralling narrative, offering readers a glimpse into a story that is rich in detail and brimming with originality from the outset. It’s the […]
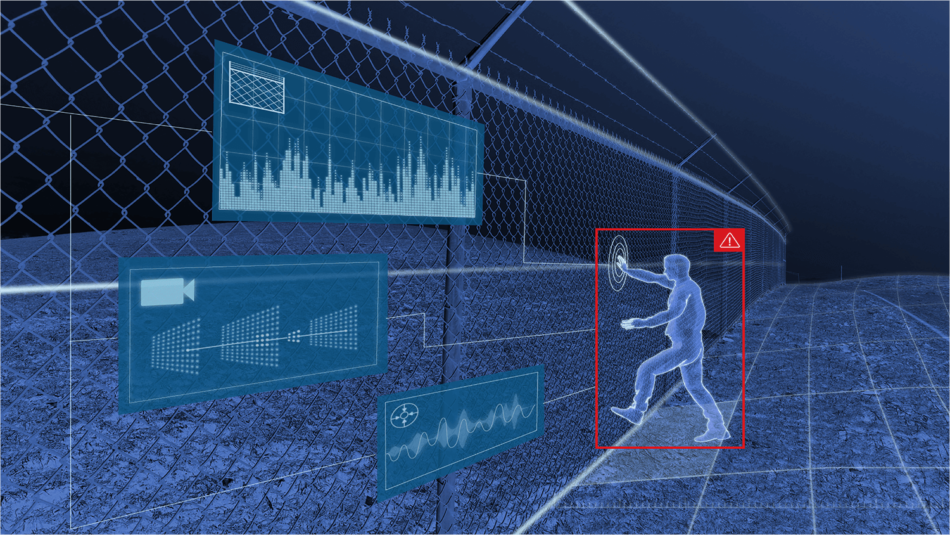
Perimeter technology sets the stage for this enthralling narrative, offering readers a glimpse into a story that is rich in detail and brimming with originality from the outset. It’s the unsung hero of cybersecurity, a guardian of the digital realm, diligently protecting our data and systems from the ever-evolving threats of the modern age.
Imagine a fortress, a protective barrier, standing vigilant against invaders. That’s the essence of perimeter technology. It’s a multifaceted approach that encompasses a range of security measures, designed to create a secure perimeter around our digital assets, preventing unauthorized access and safeguarding our data from malicious attacks.
Definition and Scope of Perimeter Technology
Perimeter technology, in the context of cybersecurity, refers to the security measures that are implemented to protect an organization’s network and systems from external threats. It acts as a barrier, much like a physical perimeter, to prevent unauthorized access and malicious activity.
Purpose and Key Elements
Perimeter technology aims to establish a secure boundary around an organization’s network, preventing unauthorized access and data breaches. It achieves this through various key elements, including:
- Firewalls: Firewalls are the cornerstone of perimeter security, acting as a gatekeeper that controls network traffic, blocking malicious attempts to access internal systems. They analyze incoming and outgoing traffic, enforcing predefined security rules to filter out suspicious connections.
- Intrusion Detection and Prevention Systems (IDS/IPS): These systems monitor network traffic for malicious activity and take appropriate action to prevent intrusions. IDS detect suspicious activity and alert administrators, while IPS proactively block attacks.
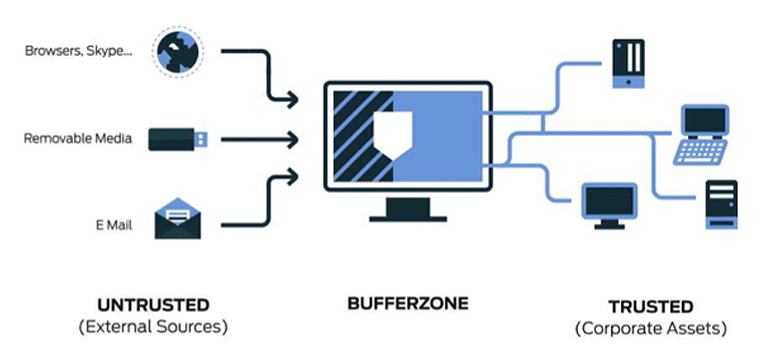
- Virtual Private Networks (VPNs): VPNs create secure connections over public networks, encrypting data and ensuring privacy for remote users accessing internal systems. This is crucial for securing access for employees working remotely or accessing sensitive information from outside the organization.
- Network Segmentation: Dividing the network into smaller, isolated segments enhances security by limiting the impact of a breach. If one segment is compromised, the attack cannot easily spread to other parts of the network.
Evolution of Perimeter Technology
The landscape of perimeter technology is constantly evolving to adapt to the changing nature of cyber threats. Modern threats often exploit vulnerabilities in traditional perimeter defenses, prompting the need for more sophisticated solutions. This evolution has led to the emergence of concepts like:
- Zero Trust Security: This approach assumes that no user or device can be trusted by default, requiring strict verification and authentication before granting access. This shifts the focus from perimeter security to granular access control and continuous monitoring.
- Next-Generation Firewalls (NGFWs): NGFWs go beyond traditional firewalls, incorporating advanced security features like application control, intrusion prevention, and threat intelligence. They provide more comprehensive protection against modern threats, including sophisticated malware and zero-day attacks.
- Cloud-Based Security: As organizations increasingly adopt cloud services, perimeter security needs to extend beyond traditional network boundaries. Cloud-based security solutions provide protection for cloud resources and applications, offering centralized management and scalability.
Traditional Perimeter Security Methods
Traditional perimeter security methods have long been the cornerstone of cybersecurity, aiming to establish a clear boundary between trusted internal networks and the untrusted external world. These methods rely on a layered approach, employing technologies like firewalls, intrusion detection systems (IDS), and virtual private networks (VPNs) to control and monitor network traffic.
Firewalls
Firewalls act as gatekeepers, scrutinizing incoming and outgoing network traffic based on predefined rules. They are typically deployed at the edge of a network, filtering out malicious traffic and preventing unauthorized access. Firewalls can be hardware-based, software-based, or a combination of both.
- Advantages: Firewalls offer a cost-effective way to protect against known threats and unauthorized access. They are relatively simple to configure and manage, and they can be easily integrated with other security tools.
- Limitations: Firewalls are primarily reactive, meaning they rely on predefined rules to identify and block threats. They are ineffective against sophisticated attacks that exploit vulnerabilities or use obfuscation techniques to bypass traditional security measures. Furthermore, firewalls can be easily bypassed by attackers who use social engineering tactics or exploit vulnerabilities in other applications.
Intrusion Detection Systems (IDS)
Intrusion detection systems (IDS) monitor network traffic for suspicious activity, alerting administrators to potential security breaches. They work by analyzing network traffic patterns and comparing them against a database of known attack signatures. IDS can be deployed in hardware, software, or as a virtual appliance.
- Advantages: IDS provide real-time threat detection and can help identify and respond to attacks that bypass traditional firewalls. They can also be used to generate security logs and reports for auditing purposes.
- Limitations: IDS are primarily passive, meaning they only detect threats but cannot prevent them. They can be overwhelmed by high volumes of traffic and may generate false positives, leading to alert fatigue and hindering effective response. Moreover, IDS are susceptible to evasion techniques used by attackers, such as stealthy attacks or zero-day exploits.
Virtual Private Networks (VPNs)
VPNs establish secure connections over public networks, allowing users to access private networks securely. They encrypt network traffic and tunnel it through a secure server, providing a secure connection between two points. VPNs are commonly used by remote workers, businesses, and individuals seeking to protect their privacy and security online.
- Advantages: VPNs offer strong encryption and secure access to private networks from anywhere in the world. They can also help bypass geographic restrictions and censorship.
- Limitations: VPNs rely on the security of the VPN server itself, which can be vulnerable to attack. They can also slow down internet speeds and may not be compatible with all applications or devices. Additionally, VPNs may not be effective against targeted attacks or sophisticated malware that can bypass encryption.
Network Segmentation and Access Control
Network segmentation divides a network into smaller, isolated segments, reducing the impact of a security breach. Access control mechanisms, such as user authentication and authorization, restrict access to specific resources based on user roles and permissions.
- Advantages: Network segmentation and access control limit the spread of malware and reduce the attack surface. They also improve network performance and security by isolating sensitive data and applications.
- Limitations: Implementing network segmentation and access control can be complex and time-consuming. It requires careful planning and configuration to ensure that all critical resources are protected. Additionally, these measures can impact network performance and require ongoing maintenance to remain effective.
Modern Perimeter Security Approaches

The traditional perimeter security model, based on physical barriers and network firewalls, has proven inadequate in the face of increasingly sophisticated cyber threats. This has led to the emergence of modern perimeter security approaches that focus on a more dynamic and adaptive security posture.
Zero-Trust Security
Zero-trust security is a security framework that assumes no user or device can be trusted by default. It enforces strict authentication and authorization policies, verifying every access request regardless of its origin.
- Key Principles: Zero-trust security operates on the principle of “never trust, always verify.” It requires strong authentication, continuous monitoring, and least-privilege access control.
- Mechanisms: Zero-trust security employs various mechanisms, including multi-factor authentication (MFA), micro-segmentation, and data loss prevention (DLP) to secure access to sensitive data.
- Effectiveness and Adaptability: Zero-trust security is highly effective in mitigating insider threats and preventing unauthorized access. Its adaptable nature allows it to adjust to evolving threat landscapes and dynamic network environments.
Software-Defined Perimeter (SDP), Perimeter technology
SDP is a technology that dynamically creates secure connections between users and applications based on identity and policy. It eliminates the traditional network perimeter and provides a secure access point for authorized users and devices.
- Key Principles: SDP operates on the principle of “least-privilege access” and “need-to-know” access control. It establishes secure connections between users and applications only when necessary.
- Mechanisms: SDP uses a combination of technologies, including tunneling, encryption, and access control lists (ACLs) to create secure connections.
- Effectiveness and Adaptability: SDP provides a highly effective and adaptable security solution, particularly in cloud-based environments. It allows organizations to securely access cloud-based applications and services without exposing their internal networks to external threats.
Key Components of Perimeter Technology

A robust perimeter security solution is not a single entity but rather a comprehensive ecosystem of interconnected components working in harmony to safeguard your digital assets. These components, each with specialized functionalities, form a multi-layered defense strategy that aims to deter, detect, and respond to threats before they can breach your network perimeter.
Firewalls
Firewalls act as the first line of defense, controlling inbound and outbound network traffic based on predefined rules. They scrutinize each data packet, comparing it against established security policies to determine whether to allow or block access. Firewalls are essential for preventing unauthorized access to your network and ensuring that only legitimate traffic is permitted.
Intrusion Prevention Systems (IPS)
IPS goes beyond simply blocking traffic by actively detecting and preventing malicious activity. These systems analyze network traffic for suspicious patterns, such as known attack signatures or anomalous behavior, and take immediate action to stop the threat. They can block connections, reset sessions, or even send alerts to security personnel.
Data Loss Prevention (DLP)
DLP solutions focus on protecting sensitive data from unauthorized access, use, or disclosure. They monitor data flows within the network and identify data that matches predefined rules, such as credit card numbers, social security numbers, or confidential business documents. When a potential data breach is detected, DLP systems can take actions like blocking the transmission, encrypting the data, or generating alerts.
Endpoint Security
Endpoint security solutions protect individual devices, such as laptops, desktops, and mobile phones, from threats. They often include a combination of technologies like antivirus software, anti-malware software, and host-based firewalls to prevent malware from infiltrating devices and protect sensitive data stored on them.
Table of Key Components
| Component | Functionality | Contribution to Perimeter Security |
|---|---|---|
| Firewall | Controls network traffic based on predefined rules, blocking unauthorized access. | Acts as the first line of defense, preventing unauthorized access to the network. |
| Intrusion Prevention System (IPS) | Detects and prevents malicious activity by analyzing network traffic for suspicious patterns. | Proactively identifies and blocks threats, enhancing the network’s security posture. |
| Data Loss Prevention (DLP) | Monitors data flows and identifies sensitive data to prevent unauthorized access, use, or disclosure. | Protects sensitive data from unauthorized access, use, or disclosure, safeguarding valuable information. |
| Endpoint Security | Protects individual devices from threats through antivirus, anti-malware, and host-based firewalls. | Secures individual devices, preventing malware infiltration and protecting data stored on them. |
Challenges and Future Directions

Perimeter security is a constantly evolving field, facing new challenges as technology advances and attackers become more sophisticated. Traditional perimeter security methods are no longer sufficient to protect against modern cyber threats. This section explores the emerging challenges to perimeter security and discusses the future trends and advancements in perimeter technology.
Emerging Challenges to Perimeter Security
The rise of sophisticated attacks and the increasing complexity of IT environments pose significant challenges to perimeter security.
- Advanced Persistent Threats (APTs): APTs are highly organized and well-funded groups that use advanced techniques to penetrate networks and steal sensitive information. They often target specific organizations and can remain undetected for extended periods.
- Zero-Day Exploits: Zero-day exploits are vulnerabilities in software that are unknown to developers and security vendors. Attackers can use these vulnerabilities to gain unauthorized access to systems before patches are available.
- Cloud Computing: The adoption of cloud computing has expanded the perimeter, making it more difficult to secure. Cloud services are often hosted in multiple data centers around the world, making it challenging to control access and monitor activity.
- Mobile Devices: The proliferation of mobile devices has created new attack vectors. Mobile devices are often used to access sensitive information, and they can be easily compromised by malware.
- Internet of Things (IoT): The increasing number of IoT devices connected to the internet presents a significant security risk. These devices are often poorly secured, making them vulnerable to attacks.
Future Trends and Advancements in Perimeter Technology
The future of perimeter security will be driven by advancements in artificial intelligence (AI) and machine learning (ML). These technologies can help organizations to better detect and respond to threats.
- AI-Powered Threat Detection: AI can be used to analyze large amounts of data and identify patterns that indicate malicious activity. This can help organizations to detect threats that might otherwise go unnoticed.
- ML-Based Security Automation: ML can be used to automate security tasks, such as threat response and incident remediation. This can free up security teams to focus on more strategic initiatives.
- Behavioral Analytics: Behavioral analytics can be used to monitor user activity and identify anomalies that may indicate a security breach. This can help organizations to detect attacks that target specific users or systems.
- Next-Generation Firewalls (NGFWs): NGFWs are designed to protect against modern threats, such as APTs and zero-day exploits. They use advanced features, such as intrusion prevention, application control, and threat intelligence, to enhance security.
- Security Information and Event Management (SIEM): SIEM systems collect and analyze security data from multiple sources. This can help organizations to identify security threats and respond quickly to incidents.
Evolving Perimeter Technology to Address Future Cyber Threats
To effectively address future cyber threats, perimeter technology must evolve to become more proactive, intelligent, and adaptable.
- Proactive Security: Organizations must move away from a reactive approach to security and adopt a proactive posture. This means implementing security controls that prevent attacks before they can occur.
- Intelligence-Driven Security: Organizations must leverage threat intelligence to understand the latest attack trends and develop strategies to mitigate risks.
- Adaptive Security: Organizations must be able to adapt their security controls in response to evolving threats. This means using technologies that can automatically detect and respond to new threats.
- Focus on User Education: Organizations must educate users about security best practices to reduce the risk of human error. This includes training users on how to identify phishing attacks, strong password management, and safe browsing habits.
- Collaboration and Sharing: Organizations must collaborate with each other and share threat intelligence to improve overall security. This can help to prevent attacks from spreading and protect the entire ecosystem.
Wrap-Up: Perimeter Technology
As the landscape of cyber threats continues to evolve, so too must our defenses. Perimeter technology, with its constant innovation and adaptation, is a critical component in this ongoing battle. By understanding the principles, components, and implementation strategies of perimeter technology, we can build robust defenses, securing our digital world and ensuring the integrity of our data.
Perimeter technology plays a crucial role in securing sensitive areas, and a key component of any effective perimeter security system is reliable hose technology. Precision Hose Technology Inc is a leading provider of high-quality hoses specifically designed for perimeter security applications, ensuring that your perimeter remains secure and protected from unauthorized access.